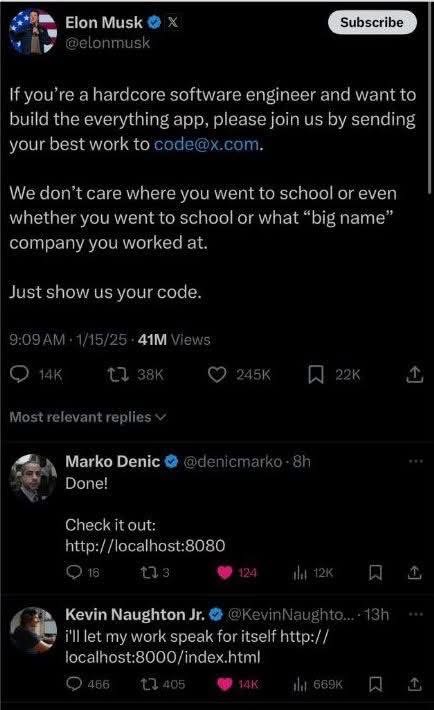
Here’s what’s happening in the thriving tech scene in Tampa Bay and surrounding areas for the week of Monday, May 26 through Sunday, June 1, 2025!
This list includes both in-person and online events. Note that each item in the list includes:
✅ When the event will take place
✅ What the event is
✅ Where the event will take place
✅ Who is holding the event

This week’s events
Monday, May 26
Remember: Monday is Memorial Day! Some meetup organizers simply schedule their events “on autopilot” (e.g. “last Monday of the month”) and forget to account for holidays.
Before you attend a meetup on Monday, May 26, check with the organizers to make sure it’s actually happening!
Tuesday, May 27

Tuesday morning at 10 a.m., online: Computer Coach presents IT Certs Help You Soar – No Degree Required. Are you ready to take your career to new heights in months rather than years? Join this webinar for an empowering webinar where they’ll show you how IT certifications can open doors to high-paying, in-demand roles in technology and beyond.
Find out more and register here.

Tuesday evening at 5:30 p.m. at Hidden Springs Ale Works (Tampa): Another exciting night of TampaTech, Taps & Tacos!
Tech – Connect & network with fellow tech industry peers
Taps – Enjoy 15% off your tab as a tech attendee
Tacos – A full taco bar… because who doesn’t love tacos?!
No speakers, no presentations — just great conversations and a Raffle (because that’s way more fun! )
Find out more and register here.

Tuesday evening at 6:00 p.m. at University Boba Tea House (Tampa): Tampa Artificial Intelligence Applications Meetup Group is hosting their weekly meeting!
Find out more and register here.
Wednesday, May 28
Thursday, May 29

Thursday at noon, online: Computer Coach presents Your Unique Value Proposition! Your unique value proposition is your secret weapon in the job search. It’s not just about what you do—it’s about who you are, what drives you, and how you solve problems. In this webinar, learn how to clearly communicate your value to recruiters and hiring managers, positioning yourself as the right fit for the right opportunity.
Find out more and register here.

Thursday afternoon at 4:00 pm at American Legion Post 38 (Tampa): It’s the Tampa/MacDill AFB Orange Call! In a military context, an “orange call” refers to an alert signaling a heightened cybersecurity state of readiness.
This orange call’s purpose is to gather and network amongst fellow communicators, guardians, and enablers of all ranks, titles, and experience levels, share resources, and seek professional development. They’ll will conduct a round table meet & greet and discuss MacDill communicators and missions, including the increasing role of cyber and the importance of defending our nation’s networks.
Find out more and register here.
Friday, May 30
Saturday, May 31
 Saturday from 10 am to 1 pm at Computer Coach (Tampa): Get started with Python at the Python for beginners workshop! Bring a laptop — we’ll help you get Python installed on it, and help you get started with your first Python programs!
Saturday from 10 am to 1 pm at Computer Coach (Tampa): Get started with Python at the Python for beginners workshop! Bring a laptop — we’ll help you get Python installed on it, and help you get started with your first Python programs!
Find out more and register here.

Gulf Coast MakerCon provides an opportunity for everyone to join together to share resources, learn a craft, hone their skills, find career and academic opportunities, try new tools and innovations, and showcasing everyone’s amazing creativity!
Find out more here.
Sunday, June 1

About this list
How do I put this list together?
It’s largely automated. I have a collection of Python scripts in a Jupyter Notebook that scrapes Meetup and Eventbrite for events in categories that I consider to be “tech,” “entrepreneur,” and “nerd.” The result is a checklist that I review. I make judgment calls and uncheck any items that I don’t think fit on this list.
In addition to events that my scripts find, I also manually add events when their organizers contact me with their details.
What goes into this list?
I prefer to cast a wide net, so the list includes events that would be of interest to techies, nerds, and entrepreneurs. It includes (but isn’t limited to) events that fall under any of these categories:
- Programming, DevOps, systems administration, and testing
- Tech project management / agile processes
- Video, board, and role-playing games
- Book, philosophy, and discussion clubs
- Tech, business, and entrepreneur networking events
- Toastmasters and other events related to improving your presentation and public speaking skills, because nerds really need to up their presentation game
- Sci-fi, fantasy, and other genre fandoms
- Self-improvement, especially of the sort that appeals to techies
- Anything I deem geeky