Month: November 2013
Sir Patrick Stewart has but one rule for using Twitter, and it’s a good one. In this video, he explains how he uses it, and how he came up with the rule.
This article also appears in The Adventures of Accordion Guy in the 21st Century.
The iOS Apprentice: Second edition for iOS 7 and Xcode 5 now available!
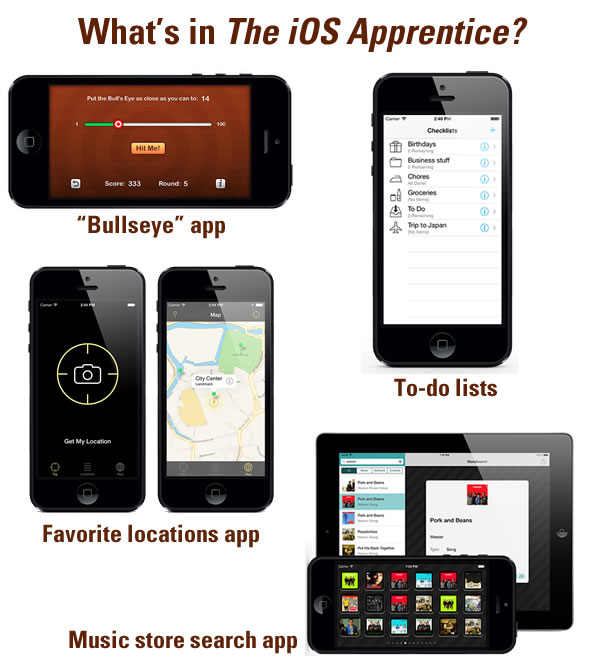
If you want to learn iOS development and need a little structure to help you get started, I strongly recommend RayWenderlich.com’s iOS Apprentice, a set of four excellent tutorials written by Matthijs Hollemans. Each tutorial walks you through the construction and completion of a full-functional iOS app. The tutorials are:
- Bullseye: A simple game app. Building it, you’ll learn about iOS’ UI controls and using them to get input from and present results to the user.
- Checklists: Learn how to make use of table views and store user data by building a “to-do list” app.
- MyLocations: Build a location-aware app, and learn more about iOS’ object model and Core Data.
- StoreSearch: An app that lets you search the iTunes Store for music. Along the way, you’ll learn how to write apps that call web services, support multiple languages, create pop-up detail screens, and build universal apps that run on both the iPhone and iPad.
RayWenderlich.com says that you don’t need any prior development experience to use these tutorials, but even a experienced developer will find them useful (you can just skip the basic programming parts, and there’ll still be a lot of info you can use). Each app builds on the lessons of the previous one. By the time you’re done building the final app, you should be able to write your own App Store-worthy apps. I can’t recommend the iOS Apprentice highly enough; I’ve found it so incredibly helpful as I learned iOS development.
The latest edition has been updated for iOS 7 and Xcode 5, and it spans over 900 pages. If you haven’t bought any of the previous editions, you can buy the iOS Apprentice for US$54, which entitles you to free updates. If you have bought an earlier edition, you can download it for free.
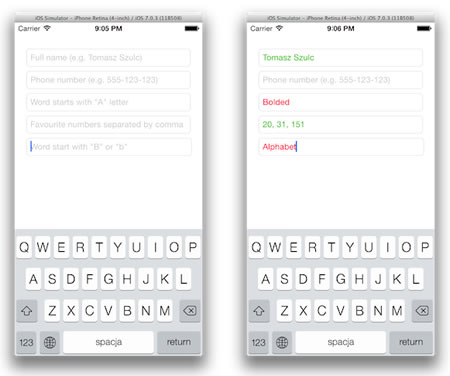
TSValidatedTextField: A text field that you can validate with regex patterns
TSValidatedTextField is a subclass of UITextField that lets you use an NSRegularExpression to specify valid and invalid input.
Typhoon: A dependency injection framework for Objective-C

Dependency injection is a fancy-pants way of describing a design pattern that removes hard-coded dependencies on collaborating objects, making code that’s easier to modify, test, and update. You can do dependency injection on your own, but it’s much easier to use a framework. Typhoon is one such framework for Objective-C, it’s ready for us right now, and their site goes into greater detail on why you might want to use dependency injection and why you might want to use their particular framework.
All sorts of basic algorithms implemented in Objective-C
And finally, if you want to see what you might have forgotten from your second-year algorithms class implemented in Objective-C, take a look at Evgeny Karkan’s EKAlgorithms. In this still-evolving GitHub repo, you’ll see these classic hits from computer science:
Array
- Index of maximum element in array.
- Find longest string in array of strings.
- Find shortest string in array of strings.
- Array reverse.
- Intersection of two arrays.
- Union of two arrays (with remove duplicates).
- Find duplicates.
- Array with N unique/not unique random objects.
- Linear search.
- Binary search.
- Bubble sort.
- Shell sort.
- Merge sort.
- Quick sort.
- Insertion sort.
- Palindrome or not.
- String reverse.
- Words count.
- Permutations of string.
- Occurrences of each character (a – z).
- Count needles in a haystack.
- Random string.
- Sieve of Eratosthenes.
- Great common divisor (GCD).
- Least common multiple (LCM).
- Factorial.
- Fibonacci numbers.
- Sum of digits.
- Binary to decimal conversion.
- Decimal to binary conversion.
- Fast exponentiation.
- Stack (LIFO).
- Queue (FIFO).
- Deque.
- Linked list.
- Graph
- DFS (depth-first search);
- BFS (breadth-first search).
- Binary search tree (BST).
Click the photo to see the repair at full size.
Remember Weinberg’s Second Law:
If builders built buildings the way programmers wrote programs, then the first woodpecker that came along would destroy civilization.
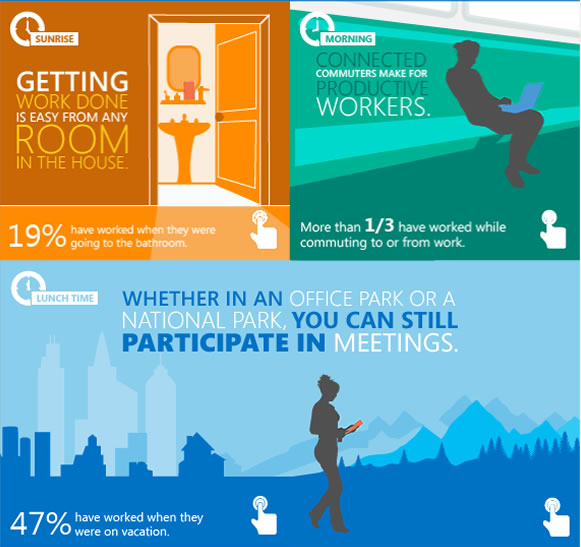
Yesterday, I posted the #GetItDone infographic produced as an ad for Office 365, which seemed to be aimed at CIOs, CTOs, and other tech decision-makers who wanted to squeeze free unpaid work from employees outside of office hours. I called it The saddest infographic in the land. Here’s a snippet:
37signals caught wind of this and create their response, a similar-looking infographic with the hashtag #WorkCanWait, which takes some well-aimed potshots at every info-nugget from the original. There’s even a feature that lets you create your own parody!
It’s part of their promotion for their book on remote work, simply titled Remote:
The saddest infographic in the land
Titled as found. Thanks, Office 365. Thanks for nothing.
Now get back to work!
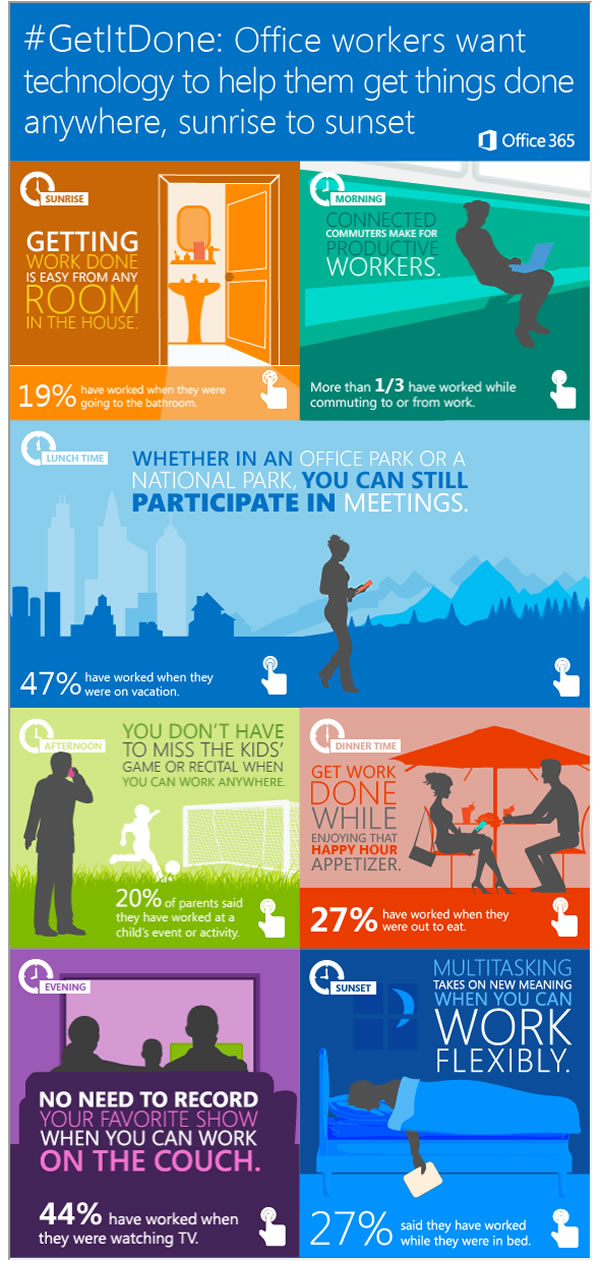
Thanks to Joe Murphy for the find!

The use of “kill switches” to prevent theft are nothing new. Many car stereo and amp units require a code to be usable after they’ve been disconnected from the battery, and you can buy switches that are either hidden or require a code that must be activated before the car can be started. Right now, you can remotely lock a stolen mobile device, but a thief can simply do a hard reset to wipe it clean, then use or sell it. What would help deter theft is a kill switch that would render the device unusable, even if a hard reset is performed.
New York- and San Francisco-based lawmakers are trying to get mobile device vendors to implement such kill switches, but they’re facing opposition from that familiar obstacle: the carriers. San Francisco district attorney George Gascón, while working with Samsung on a kill switch agreement, says that carriers including AT&T, Verizon, T-Mobile, and Sprint, who have to approve pre-loaded software, have rejected the kill switch concept. Based on emails between a Samsung exec and a developer that he saw, he says that carriers fear that a theft deterrent like a kill switch would eat into the profits they make from selling anti-theft insurance. Nice.
The public argument that carriers make against kill switches is that a malicious third party could take control of the feature and use it to disable phones. They even brought up the spectre of disabling the phones of Defense officials or police officers. They also claim that deactivated phones couldn’t be subsequently reactivated if found, which isn’t true in the case of Apple’s “Activation Lock” feature.
This isn’t the first time that carriers have stood in the way of progress because it cut into their business. It wasn’t all that long ago that they made it difficult or inconvenient to put apps on phones, saying that they could be threats to the network. The success of the iPhone changed all that; what change would it take to get carriers on board with kill switches?