
Microsoft’s recent announcement that they’re open-sourcing .NET, making Visual Studio free to small developers, and supporting development for Linux, Android, and iOS is a surprising development from one point of view, but if you were noodling with computers 30 years ago, you may think of it as a return to their oldest ways.

Those of you who grew up in the 1980s and took up programming then will remember the Microsoft logo above. You might not remember the logo they used from 1980 through 1981, making it the shortest-lived logo in their history:

Back then, a computer that you could buy from a retail store and could fit on a desktop was called a “home computer”, and more often than not, it had some version of BASIC(back when it was an acronym for Beginners All-purpose Symbolic Instruction Code), particularly Microsoft BASIC. It was either already in the machine’s ROM, or you’d load it from a plug-in ROM cartridge, cassette tape, or one of those newfangled floppy diskettes. During the “pointy logo era”, BASIC interpreters were Microsoft’s bread and butter, and if you used a version of BASIC that had the LEFT$(), MID$(), and RIGHT$() functions, you were most likely using a version of BASIC with a Microsoft license.
Some of my earliest programming experiences were on a friend’s TRS-80 Model I, which boasted a whopping 16K of RAM and Level II BASIC…

…or its bigger, beefier, disk drive-equipped successor, the Model III, which another friend had:

I would’ve loved to have a portable Model 100 back then:

…because it would’ve let me program anywhere. By this time, a Microsoft copyright notice appeared when you started up BASIC:

Computers were still largely monochrome-displaying creatures back then, so when Radio Shack released a computer that could display color, it was a big enough differentiator for them to name it the Color Computer, even though it could display a maximum of 4 colors onscreen at any given time:

It also had a version of Microsoft BASIC:

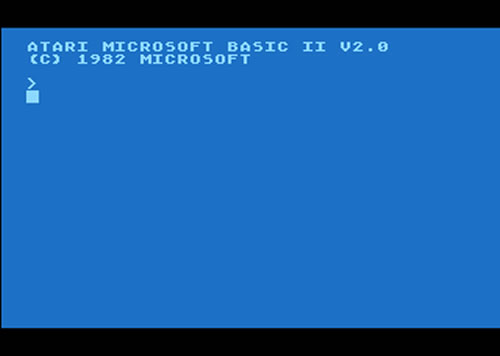
If you had an Atari 400 or 800 computer and wanted to program, you’d load up Microsoft BASIC by diskette, or if you didn’t have a disk drive, you’d use a ROM cartridge…

…pull out the manual…

…and start coding:
Terrible as the TI 99/4 was, it did have a decent enough implementation of Microsoft BASIC for me to get started with programming simple adventure games:

At my high school in the early ’80s, we had Commodore PET computers…

…and a good number of us at home had Vic-20s and Commodore 64s…

Commodore machines ran some variation of Microsoft BASIC. Bill Gates offered to license it to Commodore for $3 per unit, but founder Jack Tramiel said “I’m already married” in response. He then managed to negotiate a “pay once, no royalties” deal where they got a perpetual license for $25,000. I have a theory that experiences like this and the copying of his Altair BASIC tape led Gates to become a ruthless businessman in the late ’80s and ’90s.
Here’s a video of the Computer History Museum’s 25th anniversary party for Commodore, where Jack Tramiel tells the story of how he negotiated the deal with Gates:
We think of Apple and Microsoft as rivals, but it wasn’t always that way. Once upon a time, in the days of the
Apple ][, they were hardware/software buddies…

You could program an Apple ][ using the original BASIC that Woz implemented, but if you wanted real programming power, you used Applesoft BASIC, a variant of Microsoft BASIC. The first version was something you loaded via cassette tape:

Applesoft II came out afterwards, and it was 16K in size, which was a lot at the time. Most home computers were based on either the Z-80 processor (the TRS-80s were) or the 6502 (as Apple’s, Atari’s, and Commodore’s were), both of which had a 16-bit address bus. That meant that they could address a maximum of 64K memory locations.
A maxed-out Apple ][‘s memory was arranged this way:
- The lower 48K were for RAM. If you had a disk drive, some of this RAM was devoted to the disk operating system.
- The upper 16K were for ROM, which included the original BASIC.
It turned out that through some bank-switching magic, you could boost an Apple ][ to 64K of RAM. You could buy a 16K RAM card that would plug into one of the Apple ][‘s many expansion slots, where it would replace the upper 16K taken up by ROM. You often loaded Applesoft BASIC, Apple Pascal, or some other programming language into it, which is why this 16K card was often called a “language card”. A number of third-party vendors sold such language cards, including Microsoft:

Microsoft even sold a card that put a Z-80-based computer into your Apple ][, which let it run CP/M:

Later, when the original Macintosh came out…

…Microsoft came out with a BASIC interpreter for it…

…and Bill Gates made an appearance at an Apple event where he said that he expected that the Mac would account for half of Microsoft’s revenues in 1984:
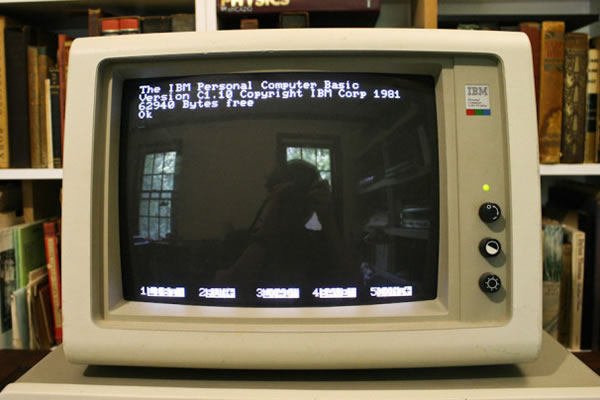
When IBM approached Microsoft for software for their new Personal Computer, they got more than just DOS (which Microsoft put together in a hurry by buying 86-DOS from Seattle Computer Products), they also got BASIC:

It was a time when so many different computing platforms were available, each with its own operating system and features. It might have been more difficult to program them, but I found that I could leap from computer to computer with ease, because Microsoft BASIC connected them all. I knew that I could take the code from books like these…

…and make it work on an Apple, Atari, Commodore, IBM PC, Texas Instruments, and TRS-80 with only a few tweaks for each machine.
I’d like to see if Microsoft can repeat this with their new open-approach, open-sourced .NET.






































