 Would you like ALL THE BOOKS pictured below for just $25?
Would you like ALL THE BOOKS pictured below for just $25?
 You can get all 18 of these O’Reilly books on AI and machine learning for a mere $25 at Humble Bundle — but only for the next 13 days (at the time of writing)!
You can get all 18 of these O’Reilly books on AI and machine learning for a mere $25 at Humble Bundle — but only for the next 13 days (at the time of writing)!
For the next four days — until 2:00 p.m. EDT on Monday, March 24, 2025 — Humble Bundle’s Computer Science the Fun Way bundle will be available, giving you 18 books for as little at $36, which puts the cost of each book at a mere two bucks!
All the books come from No Starch Press, a publisher of some great books, and the folks behind my current favorite books for my Python courses.
If you’ve tried to go past the APIs like the ones OpenAI offers and learn how they work “under the hood” by trying to build your own neural network, you might find yourself hitting a wall when the material opens with equations like this:
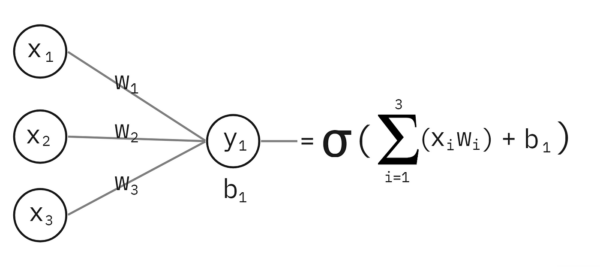
How can you learn how neural networks — or more accurately, artificial neural networks — do what they do without a degree in math, computer science, or engineering?
There are a couple of ways:
Along the way, both I (in this blog) and Tariq (in his book) will trick you into learning a little science, a little math, and a little Python programming. In the end, you’ll understand the diagram above!
One more thing: if you prefer your learning via video…
My third experiment for 2024 involves trying out the ideas from Noah Kagan’s new book, Million Dollar Weekend.
ℹ️ In case you’re wondering: my first experiment of 2024 was to turn my layoff experience into a series of articles; the second was to take a chance working with a pre-seed startup.
Why conduct such an experiment? For now, let’s just say that current circumstances make it necessary, and hey, if anyone can pull off this kind of thing, it would be me.
The general idea of Million Dollar Weekend is that you can start a lucrative business by doing the following:
The prerequisite for the Million Dollar Weekend process is a certain amount of unmitigated gall. Time and again in the book, Kagan states that two things hold people back from starting businesses:
Kagan’s methodology is to start by trying out an idea, seeing if someone will pay for that idea, and then either refining that idea or coming up with a new one and repeating the cycle.
The methodology anticipates rejection, and in fact, it says that in selling your idea, you should aim for plenty of rejections. The idea is that if you’re getting rejected often, you’re asking often, and that’s what eventually leads to success.
I’ll write more as I continue with this experiment, but for now, if you’re curious, here are some resources I can point you to:
You might also find these interviews with Kagan interesting:
ℹ️ Also in case you were wondering: This is NOT a paid promo for the book — neither Noah Kagan nor his businesses have any idea who I am or how to deposit money into my bank account. I wish they did!
…appears in Vasily “vas3k” Zubarev’s Machine Learning for Everyone, which begins with:
Machine Learning is like sex in high school. Everyone is talking about it, a few know what to do, and only your teacher is doing it.

The current “best bang for your buck” deal on AI ebooks is the 3-book version of Humble Bundle’s Machine Learning and AI 2023 book bundle, which is available for a mere one US dollar for the next 16 days.
I already own one of the three (Artificial Intelligence with Python, Second Edition), but I’m not going to complain about getting two new-to-me books at 50 cents each!
The books are:
Are you looking for an economical way to become an AI development expert? Spend a buck on these three books, get any computer made in the past dozen years with plenty of RAM (SODIMMS for old computers are pretty cheap these days), and do the exercises in the books. We’re early enough into the new AI age that if you do all these, you’ll be ahead of most aspiring AI developers out there.
From now until midnight Eastern time (UTC-4) on July 31st, Manning’s books and videos on software development and technology are selling at greatly reduced prices:
Check the out at Manning.com.
(I’m not affiliated with Manning in any way, other than I own some Manning books and get their announcement emails, which is how I found out about this.)