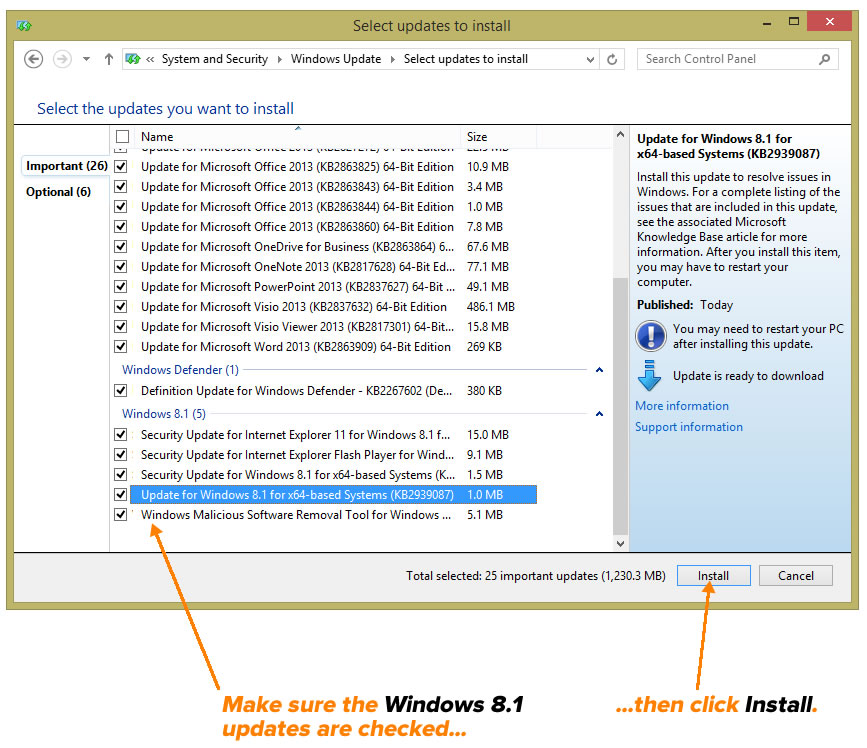
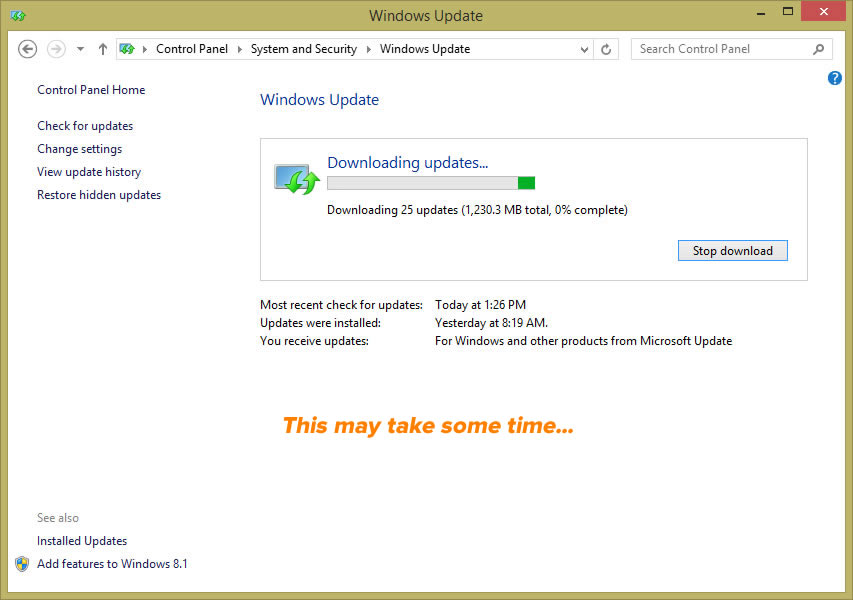
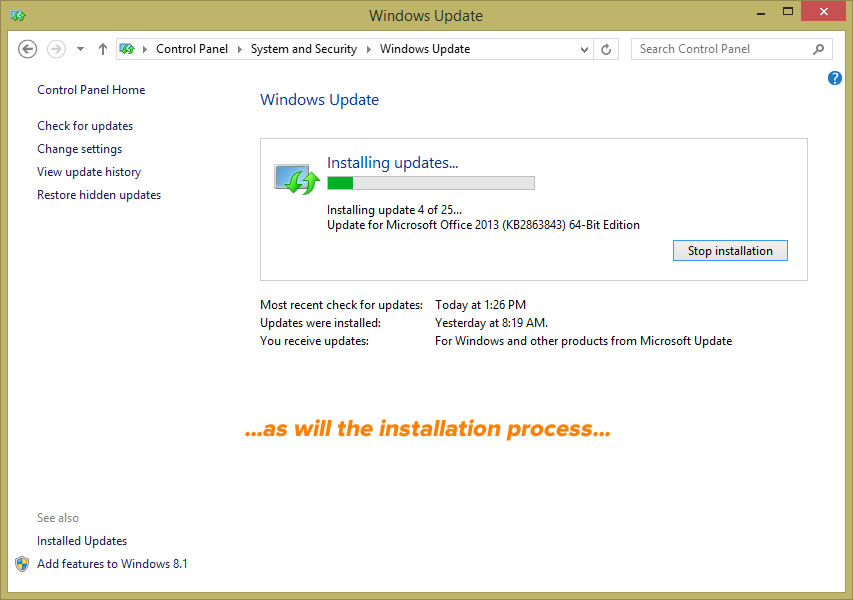
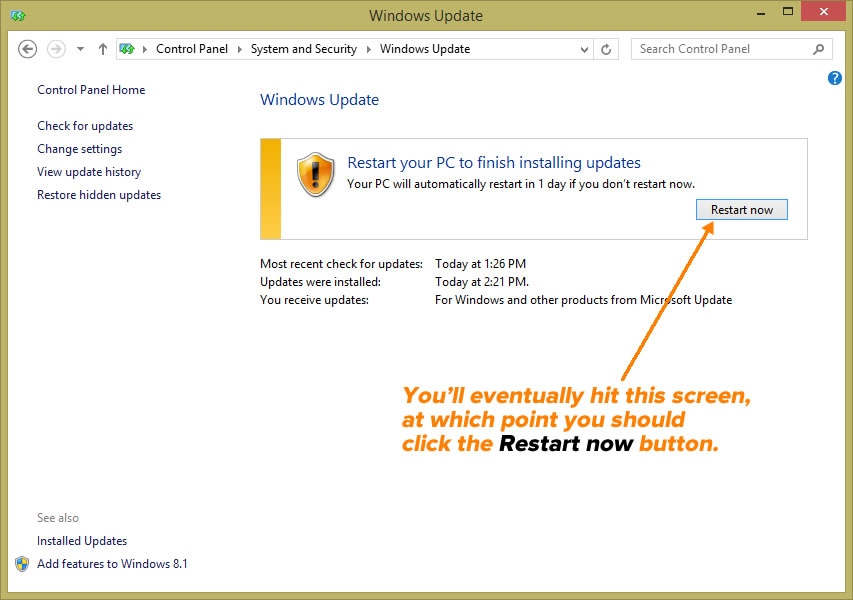
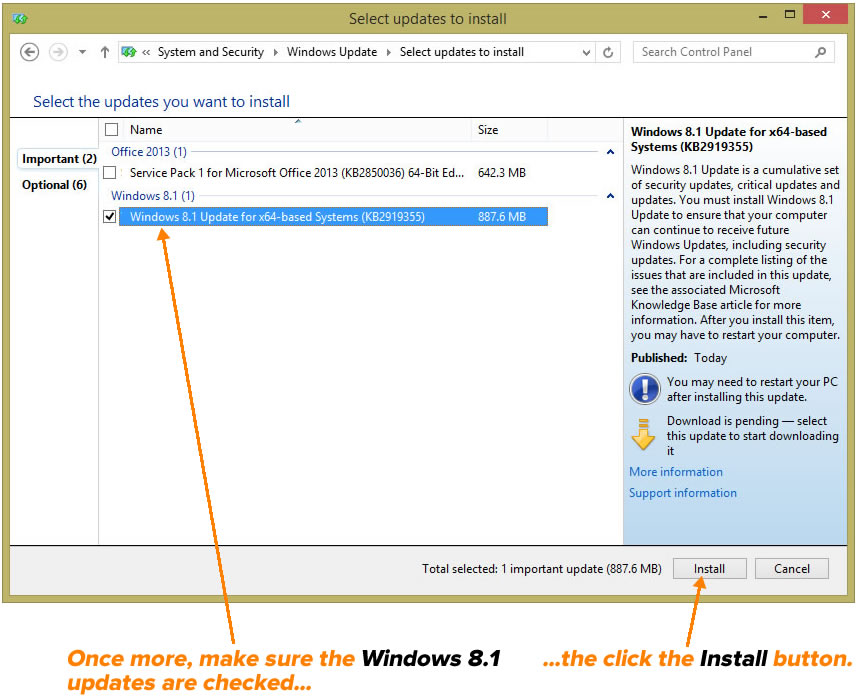
Windows Phone 8.1 Reviews
In Ars Technica, Peter Bright writes this about Windows Phone 8.1: “Windows Phone 8.1…has a lot of work to do. It needs to take further steps along the path toward Microsoft’s vision of a unified operating system. It needs to work better on a wider range of hardware to both strengthen its position at the low end and give it a chance of making inroads at the high end. It needs to also offer features: it needs to do things to get people talking about the platform while attracting both users and developers. Remarkably, Windows Phone 8.1 delivers on all fronts.”
Here’s how his review ends:
The result feels a whole lot more mature and a whole lot more capable than its predecessor. The 0.1 version bump, chosen to align the phone platform with its desktop sibling, belies the true nature of this upgrade. It is substantial, and makes Windows Phone tremendously better.
We might still wish that there were a few more apps, and that developers spoke of the platform in the same breath as iOS and Android, but even in spite of this, Windows Phone 8.1 is a polished, fun, clever, and personal smartphone platform that’s just about everyone can enjoy. It’s a magnificent smartphone platform.
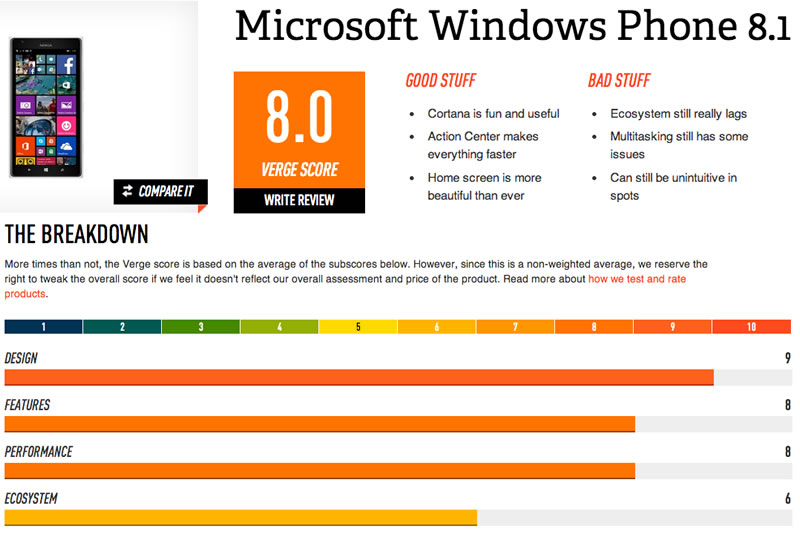
The Verge’s summary of Windows 8.1. Click to see at full size.
David Pierce reviewed Windows Phone 8.1 for The Verge. He says that with 8.1, Microsoft have an mobile operating system worth switching to; the problem is actually getting people to switch. “Microsoft is still without a truly killer, can’t-live-without-it app,” he writes, “iOS and Android may not have one either, but they have market share on their side; Microsoft needs to swing bigger.”
Pierce wraps up his review with this:
Windows Phone 8.1 is a good operating system. It can’t hide the still-lacking Windows Phone Store, which simply still doesn’t have the quantity or quality or timeliness of apps that Android and iOS do, but it goes a long way toward making Windows Phone feel competitive. It feels finished now, really for the first time. It gives Microsoft its best chance yet to attract the billions of people who haven’t yet bought a smartphone. But Microsoft hasn’t changed the game here, only proven it can play; Windows Phone 8.1 will make a lot of Windows Phone 8 users very happy but won’t make anyone at Google or Apple sweat.

In his review for Engadget, Brad Molen says with 8.1, Windows Phone feels complete for the first time. “There are no more gaping holes in its features or functionality; I can now use Windows Phone without feeling like I’m giving up something I’d otherwise enjoy on an iPhone or Android device.” As with the other reviews, he praises Windows Phone’s “Cortana” virtual assistant, the new notification center, the new gesture-sensing keyboard, and the other features that make 8.1 feel more polished than its predecessors.
He closes with:
Of course, Microsoft still has plenty of challenges ahead. After all, it’s still unclear what kind of changes will happen to Windows Phone after the Nokia acquisition is finalized, and we still haven’t seen a ton of manufacturers announce new hardware yet, despite Microsoft’s claim that there’s renewed interest in the platform. The OS has struggled to grow since its conception and is just now starting to hit double digits in market share (in certain regions, anyway). My hope is that this update ushers in a change in momentum for Microsoft. With new leadership, a better product and the company’s “One Microsoft” vision, Windows Phone 8.1 could easily be the boost the company so needs right now.
And finally, here’s how Eric Limer wrapped up his review for Gizmodo, which is tellingly titled Gloriously Good Enough:
There’s not much in Windows 8.1 to make it appealing over other options, and if you’re a true fanboy on either side of the iOS/Android divide, Windows Phone 8.1 offers little reason to switch.
But! If you are OS-curious and Windows Phone hardware calls to you—specifically the 1020’s camera magic—8.1 finally makes that a fling worth having. The inclusion of a notification center and voice assistant finally makes the entire operating system feel natural and full in a way it never did before. The update to 8.1 makes Windows Phone not only average, but inclusive to people who “grew up” with other operating systems in a way that’s really promising for the future of Windows Phone, and the future of the mobile OS power-balance on the whole.
Here are the links to all the reviews above, plus a couple more:
Battle of the virtual assistants: Cortana vs. Siri vs. Google Now

With Windows 8.1 comes Cortana, the virtual assistant that borrows not just its name, but the voice actor who played the artificial intelligence of the same name from the Halo game series. C|net’s Jessica Dolcourt has an article in which she compares Cortana against the virtual assistants from Android (Google Now) and Apple (Siri).
Before the iPhone, Android didn’t have touchscreen support

Android 2006 “Sooner” device, powered down. Click the photo to see it at full size.
One of the interesting side effects of the Apple-vs.-Samsung patent infringement suit is the exposure of confidential documents that give us a look into both companies’ thinking, strategies, intentions, and what kept them up at night. We’ve looked at some of these documents in earlier posts on this blog, from Apple and from Samsung.
Re/code has reported on the latest internal company document to be exposed, which comes from neither Apple nor Samsung, but from Android’s creator, Google. Titled Android Project Software Functional Requirements Document and dated July 6, 2006, and it’s a pretty good overview of the Android operating system as it was conceived and being implemented back around that time, six months before the keynote during which Steve Jobs introduced the iPhone.
In that document is a notable passage about Android’s approach to touchscreens at that time:
Touchscreens will not be supported. The product was designed with the presence of discrete physical buttons as an assumption. However, there is nothing fundamental in the products architecture that prevents the support of touchscreens in the future.
Instead, what they envisioned was a product similar to the flagship smartphones of that era, with physical keyboard, “pick up” and “hang up” buttons, and a D-pad for navigation. Here’s Steve Jobs from the 2007 iPhone keynote, showing these phones:

Seen today in 2014, it’s no longer a set of flagship smartphones, but a “Where are they now?” gallery of once-dominant smartphone manufacturers.
Here’s the Android hardware reference device, codenamed “Sooner”, which would’ve been the model for Android hardware partners to follow:

Android 2006 “Sooner” device, powered up. Click the photo to see it at full size.
Things changed after the iPhone keynote. Here’s an excerpt from Fred Vogelstein’s book, Dogfight: How Apple and Google Went to War and Started a Revolution:
On the day Jobs announced the iPhone, the director of the Android team, Andy Rubin, was six hundred miles away in Las Vegas, on his way to a meeting with one of the myriad handset makers and carriers that descend on the city for the Consumer Electronics Show. He reacted exactly as DeSalvo predicted. Rubin was so astonished by what Jobs was unveiling that, on his way to a meeting, he had his driver pull over so that he could finish watching the webcast.
“Holy crap,” he said to one of his colleagues in the car. “I guess we’re not going to ship that phone.”
And they didn’t.
Here’s the full Android Project Software Functional Requirements Document:




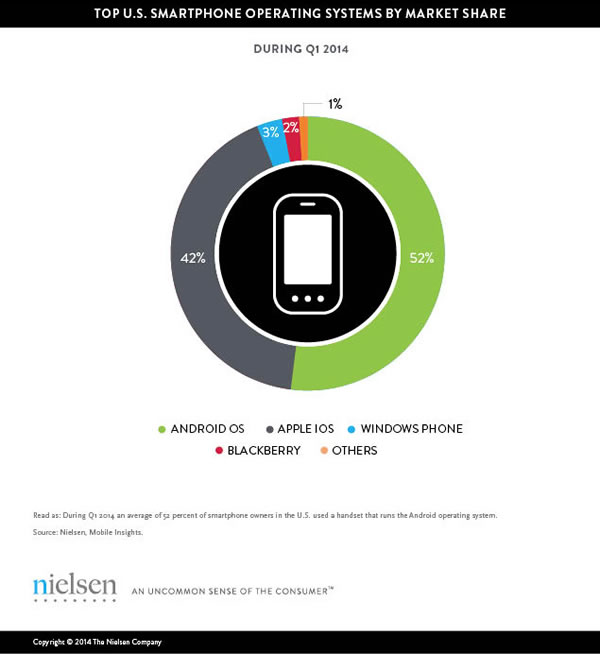
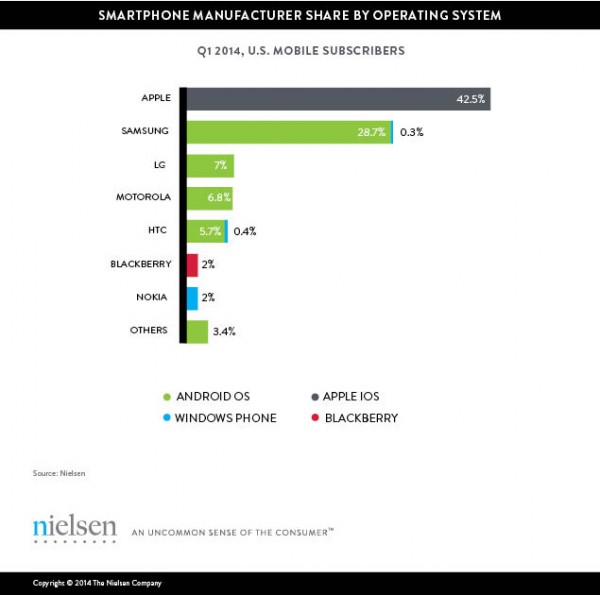















 Getting the hang of GCD
Getting the hang of GCD