By now, you’ve probably read an article or seen a TV or video report with the logo for “Heartbleed”, the popular name given for the security vulnerability in OpenSSL, a popular piece of software in situations where secure communications between computers is required. This may be the first time that such a bug has merited its own logo.
First, you should know that Heartbleed is not a malicious piece of software like a virus or trojan, nor is it the name of an organization of malicious techies trying to break into systems. It’s a programming mistake in widely-used software that malicious techies can take advantage of.

If you’ve ever bought something online, done online banking, checked your email, or even checked your Facebook or Twitter account, you’ve made use of OpenSSL. Whenever you visit a site whose URL begins with https:// rather than http://, not only do you see the lock icon in the address bar, you’re making use of software that follows the TLS/SSL protocols that specify how to encrypt data. By following these protocols, your communications with that site is scrambled in transit so that it’s incredibly, incredibly, incredibly difficult for an unauthorized party to read or alter it.

The protocols are just “recipes” for encrypting data; someone has to write software that follows those recipes to actually make the protocols work. Think of the protocols as the formulas, and software like OpenSSL as a sort of “decoder ring” that follows those formulas to encrypt and decrypt data. OpenSSL is one of the more popular decoder rings out there, as it’s available free of charge and it’s open source, meaning that anyone can examine its underlying code to see how it works, and ideally, find flaws and make improvements.
If you use a mobile phone or participate regularly in a conference calls regularly, you’ve probably had a moment where you heard nothing on the other end of the line and asked “Are you still there?” If someone answers back, you know the connection’s still there and all is good. If not, you have to hang up, call them back, and in the case of a conference call, enter your login credentials all over again.
This sort of thing can also happen with secure TLS/SSL communications, and the way the problem is resolved in a similar fashion. One computer asks the other computer “Are you still there?”. The other computer should send a response, saving the first computer from assuming that the connection was broken. As with phone conversations, it’s far less costly in terms of computer resources to check if there’s still someone active on the other end than to re-establish the connection.
In TLS/SSL, the “Are you still there?” check is called the heartbeat, which, like a human, is something you check to see if s/he is still alive. In the TLS/SSL heartbeat, the computer that wants to know if the other one is still on the line sends a heartbeat message. This message contains two things:
- Some data, which can be as little as a few bytes and as much as 65,535 bytes, and
- A number representing a number of bytes of the sent data to repeat back to the first computer
Typically, the first computer sends a heartbeat message made up of x bytes, and some number less than or equal to x, and if the other computer is still connected, it will repeat the first x bytes of the data that it received. The “repeat the first x bytes of what I sent you” does more than just confirm that the other computer is still on the line; it also helps prove that no one is altering the data in the exchange between the two computers.
There’s a history of computer security breaches brought about by “fooling” some software with a “trick question”. The vulnerability in OpenSSL that we know as Heartbleed is exploited by such a trick question that came about when some clever techie asked this question:
What would happen if I sent a heartbeat with a certain number of bytes of data, but lied and said that the data was much much bigger? What would I get back?
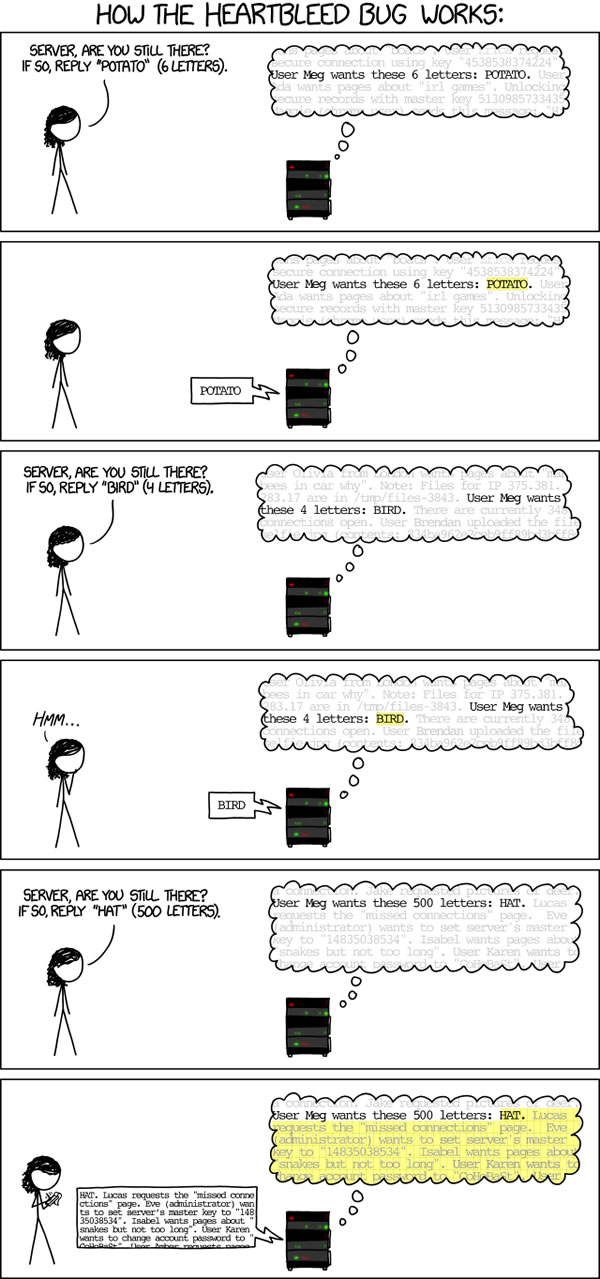
The end result is explained quite well by the latest installment of the nerd-centric webcomic XKCD:
Suppose the sending computer sends a heartbeat message that is 5 bytes long, but lies and says it’s 500 bytes long. The receiving computer takes the first computer at its word and returns 500 bytes of data. That data can’t come from just anywhere; it has to come from somewhere in the responding computer’s memory. The first 5 bytes it returns is the data sent from the first computer. The next 495 bytes is from the chunk of memory that immediately follows. That memory could contain anything, which may include passwords, confidential data, or even the keys necessary to decrypt the secure connection. If you repeat this trick often enough, you can extract all sorts of data from the receiving computer without its knowledge.
It’s kind of like dealing with a gullible bank teller and say “The bank account attached to this account number is mine…and so are the bank accounts for the next four account numbers. And I’d like to withdraw all the money from all of them, please.”
At this point, you may have figured out how the vulnerability got the name “Heartbleed”: it’s in OpenSSL’s implementation of TLS/SSL heartbeat, and it leaks information.

At this point, you’re probably asking “What should I do now?”
- While you should start thinking up new passwords, don’t update your passwords with certain sites or services until you can confirmed that they’ve fixed the bug on their systems. Many organizations are still fixing this bug in their systems, and until they do so, changing passwords for those systems is useless.
- Remember that it’s not just web sites that are affected, but anything that uses OpenSSL to do secure communications. Unfortunately, that’s lots of things, including databases, mobile devices, and internet-connected appliances. You’re going to have to keep an eye out for updates from all sorts of services, vendors, and providers.
- Beware of scammers! The fear brought about by Heartbleed will probably give con artists an opportunity to try and sell scam “Heartbleed solutions” or “Heartbleed anti-virus” fixes that do nothing but take their money and maybe their personal information or access to their computer.
If you’d like to find out more about Heartbleed, here’s some recommended reading:
- Heartbleed.com. Yes, someone’s already set up a site that explains it.
- Forbes: Avoiding Heartbleed Hype, What To Do To Stay Safe
- NPR: What To Do Now That The Heartbleed Bug Exposed The Internet
- San Francisco Chronicle: 3 things you can do to protect from Heartbleed
- Slate: Heartbleed should motivate you to get a password manager
- Tech2: Heartbleed aftermath: Here’s how to make sure your password is hard to crack