I’ve just been informed that I’ll be one of the speakers at the 2025 edition of KCDC — Kansas City Developer Conference — which takes place August 13 through 15!
What is KCDC?
This will be the 16th KCDC, and it’ll take place at the Kansas City Convention Center in downtown Kansas City, Missouri.
KCDC draws 2000+ attendees each year and features tracks for the following topics:
- Architecture
- AI and Data Science
- Cloud
- Data
- DevOps
- Human Skills
- Java
- JavaScript
- Methodologies and Process Management
- .NET
- Other Technologies
- Security
- Testing and QA
- UI/UX and Design
My talk
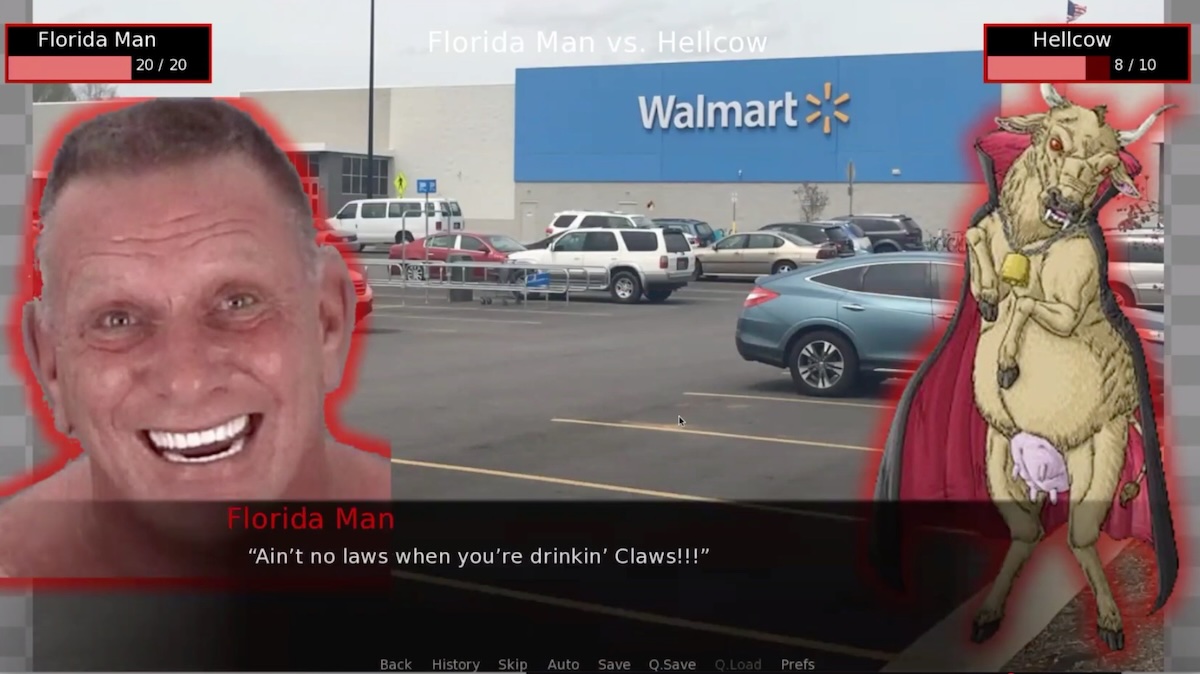 My talk, titled The Best, Most Fun Python Platform You’ve Never Heard Of, is a programmer’s introduction to the powerful, fun, and all-too-often-ignored Ren’Py. While Ren’Py is called a “visual novel engine,” I prefer to think of it as the fastest, most fun way to create Python applications.
My talk, titled The Best, Most Fun Python Platform You’ve Never Heard Of, is a programmer’s introduction to the powerful, fun, and all-too-often-ignored Ren’Py. While Ren’Py is called a “visual novel engine,” I prefer to think of it as the fastest, most fun way to create Python applications.
Here’s the description for my talk:
Python’s occupied the number one spot on the TIOBE Programming Community Index for the past couple of years, and it’s the preferred programming language in for AI and data science. Perhaps you’ve been thinking about learning it, but the thought of having to do another set of “Hello World” style exercises is filling you with dread. Is there a more fun way to get up to speed with Python?
Yes, there is, and it’s called Ren’Py. It’s billed as a visual novel engine and often used for writing dating simulation games, but it’s so much more than that. It’s a platform that lets you code in Python (and more) and deploy to desktop, web, and even mobile platforms, and with a fraction of the effort required by React, Vue, or Angular. It’s a fun framework that’s been used to produce games you can find on Steam, but it’s got applications well beyond amusement.
In this session, we’ll look not just at the basics of Ren’Py development, but the building of a dating game based on KFC’s official game, “I Love You Colonel Sanders,” a simple turn-based combat game starring Florida Man, and building mobile apps in a way that’s less frustrating than usual.
Chris Ayers is speaking too!
Better still, I won’t be the only Tampa Bay geek speaking — Chris Ayers will be there too, and he’ll be delivering his talk, The Power of Dev Containers and GitHub Codespaces:
Dive into the future of software development with our session on Dev Containers and GitHub Codespaces. Dev Containers bring reproducibility and consistency across any platform with Docker, simplifying project onboarding and setup. GitHub Codespaces takes this a step further, offering scalable, cloud-hosted development environments, accessible from anywhere.
In this session, you’ll gain insights into:
- Dev Containers Fundamentals: Understand their role in creating consistent development environments.
- GitHub Codespaces Integration: Explore how Codespaces enhances Dev Containers, providing flexible, cloud-based development.
- Practical Implementation: Learn to configure Dev Containers for your projects, including tool installation, VS Code extensions, port forwarding, and software setup.
- Maximizing Codespaces: Discover how to customize Codespaces for remote development efficiency.
François Martin will be there!
If you were at the March Tampa Bay Java User Group meetup, you saw François Martin deliver a presentation with a not-at-all-controversial title: Why Software Testing is a Waste of Time.
Anitra and I had the pleasure of taking him around Tampa while he was in town, and I even lucked out by being able to catch up with him for dinner while we were in Greece earlier this month!
He’ll deliver two talks at KCDC:
- 82 Bugs I Collected in a Year You Won’t Believe Made It to Production
- How writing just one import the wrong way slows down your website
…and yes, I’m bringing the accordion.