Over at Ars Technica, the always bang-on Cyrus Farivar has a great article titled How Zynga Went from Social Gaming Powerhouse to Has-Been. Zynga made their fortune — which eventually disappeared — by perfecting the moment of “The Pinch”, which is that point in time when you can make the switch from free to hitting up the customer for money.

I became terribly familiar with this concept during my days at OpenCola, which was during the Dot-com Bubble. A manager I used to work with there always talked about the importance of the moment when you yanked away “The Carrot” — the thing that lures customers — and switched to “The Stick”, which was your means of extracting money from them. Whenever you came up with a product idea, the first thing he’d ask is “Where’s The Stick?” “The Stick” ended up in our everyday vocabulary, and never to describe something nice. For instance, when we’d go catch a movie after work at the nearby Sony Metreon (as it was called back then), we’d look around and say “This place is all Stick“.

Zynga made its fortune by wholesale copying. FarmVille is a copy of Farm Town, and Mafia Wars is just Zynga’s own version of Mob Wars. It’s hard-coded into Zynga’s DNA. It’s through an ex-employee that we know that CEO and co-founder Mark Pincus infamously said:
“I don’t fucking want innovation. You’re not smarter than your competitor. Just copy what they do and do it until you get your numbers.”

Games are — at least as far as sane people are concerned — supposed to be fun. The article has quotes from developers who remarked that fun wasn’t really part of the equation.
Here’s FrontierVille developer Slade Villena, describing the tension between making a game that made money and a game that was fun to play:
“During my five-month mark, it started turning sour when we were pushing a lot of code that was destroying the ecosystem—they were not fixing bugs,” he said. “At one time, I had 10,000 players trapped inside a quest. 10,000! The attitude was ‘Don’t worry about them.’ [Management] would rather grab new players, keep them for three months or so, get $5 to $10 from them, and those players would quit and leave.”
He was encouraged by management to make a certain item in FrontierVille more plentiful. The item would allow you to complete a quest directly, but you’d have to spend money to get the item. From the article:
“I wanted to lower the drop rate [the frequency with which the item appeared in the game], to make it statistically possible to get this item, to keep it scarce,” Villena said. “But then it started happening to every single item in FrontierVille. The main purpose of them putting [the rate] up so high was so people could spend the tokens, and the strategy for you to make a profit was to get players to spend those tokens as much as possible. You’re reinforcing a negative attitude, rather than reinforcing a positive attitude so people keep playing the game.”
Another developer quote in the article comes from Jason Pyke, who worked on Party Place and the never-released FarmVille 2 Mobile:
“You could always fight back, but ultimately what it came down to was: I could always argue that this would make the game fun, but I had a PM tell me—many times—that they ‘couldn’t get data on fun.'”

I’m not surprised by anything in the article. That’s all due to my participation in a panel discussion at the 2010 DIG Conference (DIG is short for digital and interactive gaming), a conference on videogames held in London, Ontario. I was a Microsoft developer evangelist then, and the panel was titled The New Social Gaming Paradigm Panel. One of my fellow panelists ran a company that not only made games like Zynga, but strove to emulate Zynga. My position was that Zynga epitomized a lot of what was wrong with the way people were making games. At one point, we had an exchange that went like this (I’m quoting from memory):
Me: But what about fun?
Evil, Zynga-worshipping soulless ghoul: Fun. Doesn’t. Make. Money.
Me: Of course it does! People buy Grand Theft Auto, and Rock Band and Angry Birds because they’re fun.
Evil, Zynga-worshipping soulless ghoul: You can make more from those games if you’d actually build it little poison pills into the game that you can monetize. Make them even more addictive. Make them viral.
Me: Look at the words you’re using. Poison. Addictive. Viral. In the world of medicine, these are all bad words. You never once used nice words like “fluffy” or “chocolate”. And you practically spat when you said the word fun. Games should be fun, and gamers should be treated with respect by game makers. [Turning to audience] I want the record to show that the Microsoft guy is the ethical one in this argument right now.
That’s one of my proudest moments as a Microsoftie.
Be sure to read Cyrus’ article, and learn from Zynga’s terrible example.













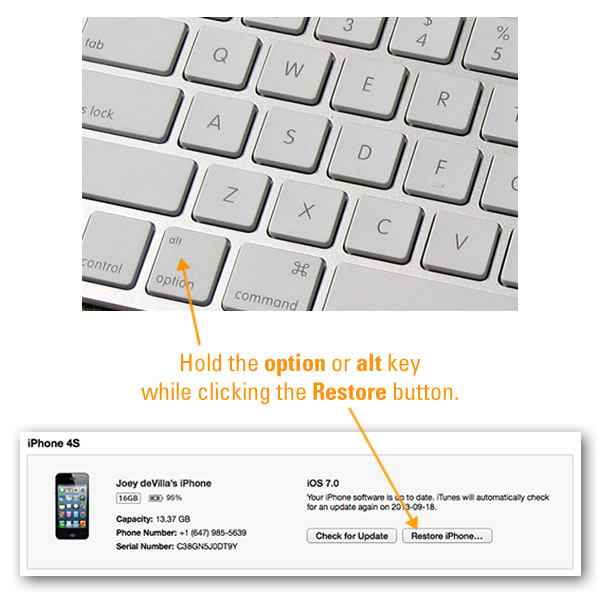
 With the announcement of
With the announcement of