
Mozilla needs to adopt this logo. Much cute! So HTML5!

Mozilla needs to adopt this logo. Much cute! So HTML5!

You’d be right to take Paul Thurrott’s latest pronouncement that Windows Phone turned the corner in 2013 with a grain of salt. He’s always been willfully, blindly enthusiastic about all things Microsoft-related, and even when it was my job to evangelize Microsoft technologies, I went out of my way not to refer to any of his pieces because he was just embarrassing. After all, he’s the guy who said this just before the release of the iPhone 3G:
There is talk of an iPhone-like Internet Tablet or the long-rumored Mac Tablet, but I think Microsoft’s failure in this category should be a warning sign: What, exactly, is the market for such a toy? There is none.
He also said this in his “first impressions” review of the iPad, which has since been deleted. Luckily for us, and thanks to the Internet Archive’s Wayback Machine, it’s been preserved for posterity:
Anyone who believes this thing is a game changer is a tool.
All that being said, he is right about one thing: Windows Phone has turned the corner. It’s just that Thurrott is talking about a bright future; I’m talking about a platform whose chances went from slim to…well, a little better than slim.
In the brutal, tooth-and-nail fight against BlackBerry for a distant third place in the mobile OS market, Windows Phone won. Winning by counting on your competitor having a massive aneurysm in the middle of the game isn’t the most practical option, but at this point, Microsoft should take any victory it can get.
With analysts like Gartner telling enterprises to ditch BlackBerry and mobile tech consultants looking to make a pretty penny on migrations from BlackBerry to other, more viable mobile platforms, Windows Phone is positioned to move out of fourth place, which is certain death in a market that barely has the capacity to deal with three big players.
If you filter through the fanboyism and hyperbole in Thurrott’s article (“the overall trend is positive for Microsoft and negative for Apple”), you can glean some useful information suggesting that Windows Phone could eke out a reasonable existence as a third-place player:
Microsoft’s goal for 2014 should be to secure Windows Phone’s third-place position and getting as close as possible to a double-digit share of the smartphone platform market. They’ve got a shot at this, with Nokia’s well-designed phones (which have amazing cameras), some pretty cleaver features in the design of the Windows Phone OS, and if they can convince more developers to build for their platform (which does have some really nice development tools). It won’t be the rosy picture that Thurrott paints, but it will be survival.

Even though it the FCC’s lifting of the ban on in-flight calling seems pretty assured — FCC Chairman Tom Wheeler seems quite hot to trot to remove it — it doesn’t guarantee that you’ll be able to make calls on just any flight. It’s still up to each individual airline to decide whether or not to allow in-flight calls, and it requires the installation of onboard technology that acts as a mini cellular tower.
USA Today reports that Delta Air Lines CEO Richard Anderson announced in a memo to employees:
Delta will not allow cellular calls or internet-based voice communications onboard Delta or Delta Connection flights.
Our customer research and direct feedback tell us that our frequent flyers believe voice calls in the cabin would be a disruption to the travel experience. In fact, a clear majority of customers who responded to a 2012 survey said they felt the ability to make voice calls onboard would detract from – not enhance – their experience. Delta employees, particularly our in-flight crews, have told us definitively that they are not in favor of voice calls onboard.
While they’re against in-flight voice communications, Delta are most certainly not against the use of portable electronics throughout the flight. Along with JetBlue, they were one of the first airlines to get their fleet certified for gate-to-gate use of lightweight devices such as smartphones and tablets. They still request that larger, heavier electronics, such as laptops, be stowed during takeoff and landing, but that’s related to the possibility of them getting launched in the event of a sudden change in altitude, not interference. As long as your use of electronics is silent to other passengers, Delta appears not to have a problem with it. If you need to make a voice call on a Delta flight, you’ll have to do it the way we do now: either until they close the door before the flight, or immediately after wheels-down at the destination city.
Delta’s 2012 customer survey isn’t the only one showing Americans’ strong preference for banning in-flight voice communications. A study conducted by Quinnipiac University shows the same preference:
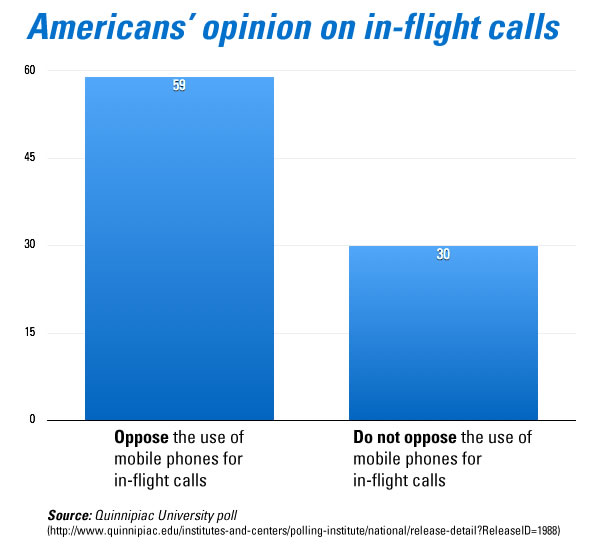
As far as I’m concerned, Delta’s decision is good news. Now if they could only get past their “Least respected brand in America” status…
Photo by Amanda Palmer. Click the photo to see the source.
Update: I found the origin of the photo — that’s Amanda Palmer. In her own words:
going to give a speech to a bunch of women at microsoft in seattle.
very nervous.
jason webley lent me an artistic helping hand so i wouldn’t feel so out of place.
everyone will like me
If you’re tech-inclined and looking for an amusing Twitter account to follow, I recommend the parody account Bored Elon Musk. He’s the new DevOps Borat (who hasn’t updated since April 5th).
Here’s the latest Bored Elon Musk post as of this writing — it’s a Venn diagram that very simply explains modern web design. As one observant wag noted in response, the area where the circles overlap should be much larger…
Click the picture to see the source.

And by “the right way”, I mean “as the designers intended”. And since they’re not HP designers, they’re more than likely to be right.
This has been floating around the internet for the past couple of days, and I’m surprised that even today, several years after Apple introduced this style of MacBook power adapter, many people still don’t know this trick for effectively wrapping the cords to easier transport. It’s simple:
…and that’s it!
Click the screen shot to see it at full size.
…I’m taking an old friend (in new form) out for a test drive. More later.