iPass and MobileIron’s 2013 Mobile Enterprise Report
Over at my company, CTS, we’re taking a close look at the numbers reported in the Mobile Enterprise Report put out jointly by iPass and MobileIron. Based on a survey of IT pros at the director level or higher (50% of whom worked for companies with more than 1,000 employees) conducted from December 2012 and January 2013, it reflects what we’ve been seeing in the enterprise.
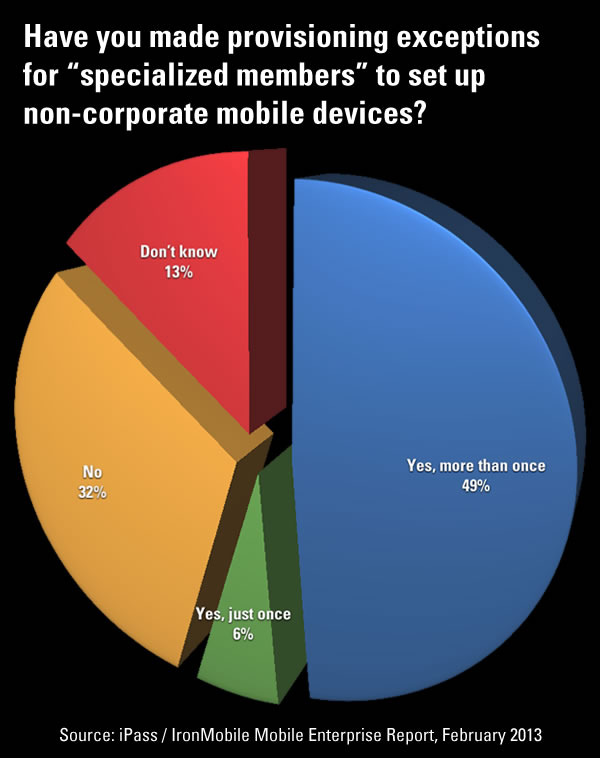
If you talk to enough IT pros and sysadmins, you’ll eventually notice the same story being told again and again: there’s a lot of rule-bending when it comes to the Big Kahunas at a company. Of the people surveyed, nearly have said that they’ve made exceptions to the rules for provisioning mobile devices to “specialized members” of the company. By “specialized”, they probably mean “people with the power to fire me, or at least make my work life very, very miserable”.
Some other notable stats and observations from the report:
- BYOD is catching on:
- 56% of respondents say they changed their corporate guidelines in the past year to be more accommodating of employees’ personal devices.
- 81% accommodate personal devices in the office.
- 54% have formal BYOD policies, and more organizations allow BYOD than have policies for it.
- Phone preferences:
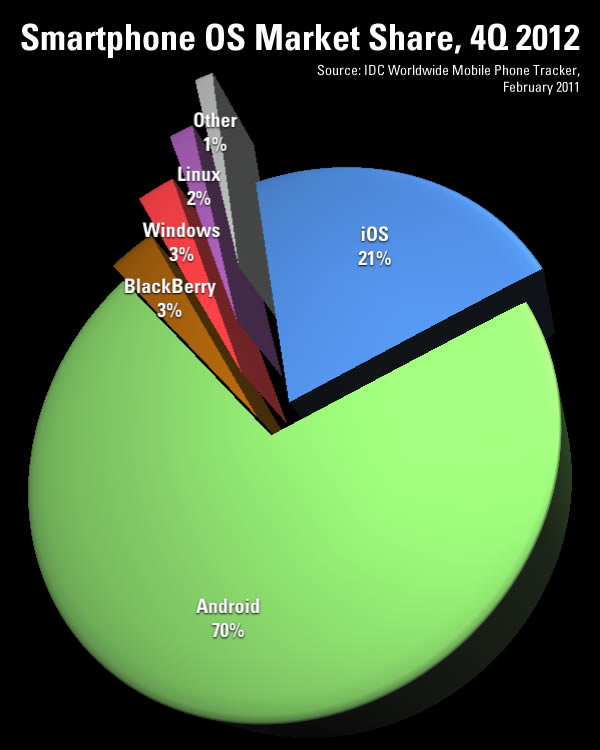
- The iPhone surpassed BlackBerry devices as the most popular in terms of corporate IT support.
- Windows Phone 8 gaining favour of BlackBerry 10? 45% of IT managers surveyed plan to support Windows Phone 8 devices; 34% plan to support BlackBerry 10.
- Tablet usage is up in all non-executive departments, especially legal, HR/administration and finance/accounting.
- The iPad is the top choice of tablets, with support from 73% of the companies surveyed.
- Also noteworthy:
- 55% of the companies surveyed had mobile device security issues last year, mostly having to do with lost or stolen phones.
- 55% of IT managers use wifi connectivity apps for productivity purposes. Wifi apps were the most widely-used out of 10 different types of enterprise mobile apps. The second most widely-used: secure email.
We’ll take another look at this report in a later article. In the meantime, if you’d like to read it for yourself, you can download it from this page. (It’s free; you’ll just have to provide some contact info.)
Citrix’s Mobile Usage Survey: We’re Really Attached to Our Mobile Devices
 A survey commissioned by Citrix and conducted by Wakefield Research shows the level to which people are attached to their smartphones. Among the numbers gathered from over 1,000 adult Americans in January 2013 were:
A survey commissioned by Citrix and conducted by Wakefield Research shows the level to which people are attached to their smartphones. Among the numbers gathered from over 1,000 adult Americans in January 2013 were:
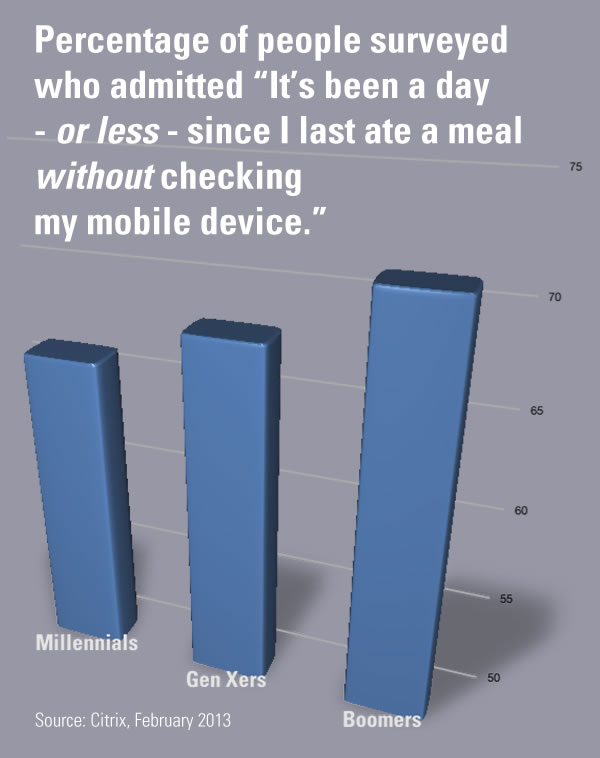
- Mobile devices as mealtime reading material: 69% of the mobile device owners surveyed said that it had been a day or less since they last ate a meal without checking their mobile device. It may seem like a phenomenon particular to Gen Y, but with 66% of them agreeing with that statement, they’re behind Gen X (68% said that this was true) and the Baby Boomers (71%).
- Mobile devices as blackmail material: Among the mobile device owners in the survey who recorded an embarrassing video of someone in 2012, 52% are saving it to share with others in 2013. That’s a bit creepy.
- Mobile devices as gauges of patience: 30% of survey respondents said that they wouldn’t wait longer than 8 seconds for a page to load, after which they’ll move onto something else. 72% of respondents said that slow downloaded would cause them to abandon downloading a large file.
- Mobile devices as communication devices? Maybe not: 64% of the people surveyed said that the primary reason they used a mobile device was “to keep myself from being bored”. Half that number — 32% — said that the primary reason was “to bring friends or family together”.
For more, see Citrix’s news release, titled Survey Shows Americans Treat Mobile Devices as Best Friends.
Citrix Bytemobile’s Feb. 2013 Mobile Analytics Report: What Mobile Traffic Data Tells Us
Bytemobile — now called Citrix Bytemobile since they were acquired — recently released a mobile analytics report that looked into mobile subscriber behaviour and QoE (Quality of Experience) for mobile services. Based on data traffic from “a global cross-section of Citrix Bytemobile customers’ mobile networks”, it contains a number of findings, including:
- On any given day, out of every 10 smartphone subscribers:
- 6 will look up information: news, weather, maps, blogs
- 4 will open a web browser
- 4 will use a social network app
- 3 will use Facebook
- 3 will engage in ecommerce
- 3 will be be served a mobile ad
- 2 will visit the App Store
- 2 will watch mobile video content
- 1 will use iTunes
- 1 will use YouTube
- 1 will use Twitter
- Data usage:
- Approximately 50% of mobile web pages download in 8 seconds or less across wireless networks worldwide. Remember that 30% of the respondents from the Citrix survey mentioned above said that they wouldn’t wait longer than 8 seconds for a page to download before moving on to something else.
- Tablets generate more data than smartphones; iPads, triply so. On average, a network-connected tablet generates 3 times more data than a smartphone, and iOS tablets generate more than 3 times the data of Android ones.
- Video accounts for more than 50% of total mobile data traffic on wireless networks, even though only 20% of mobile subscribers watch video on their devices. Mobile video watchers watch an average of 2 minutes of video at a time, which is double that of the Bytemobile Mobile Analytics Report from February 2010.
For more, get Citrix Bytemobile’s February 2013 Mobile Analytics Report (free registration required).




















 Around the time that Jobs, Wozniak, Gates, and Allen were dreaming up these unlikely schemes, I was a teenager living in Ames, Iowa. One of my friends’ dads had an old MGB sports car rusting away in his garage. Sometimes he would actually manage to get it running and then he would take us for a spin around the block, with a memorable look of wild youthful exhiliration on his face; to his worried passengers, he was a madman, stalling and backfiring around Ames, Iowa and eating the dust of rusty Gremlins and Pintos, but in his own mind he was Dustin Hoffman tooling across the Bay Bridge with the wind in his hair.
Around the time that Jobs, Wozniak, Gates, and Allen were dreaming up these unlikely schemes, I was a teenager living in Ames, Iowa. One of my friends’ dads had an old MGB sports car rusting away in his garage. Sometimes he would actually manage to get it running and then he would take us for a spin around the block, with a memorable look of wild youthful exhiliration on his face; to his worried passengers, he was a madman, stalling and backfiring around Ames, Iowa and eating the dust of rusty Gremlins and Pintos, but in his own mind he was Dustin Hoffman tooling across the Bay Bridge with the wind in his hair.






