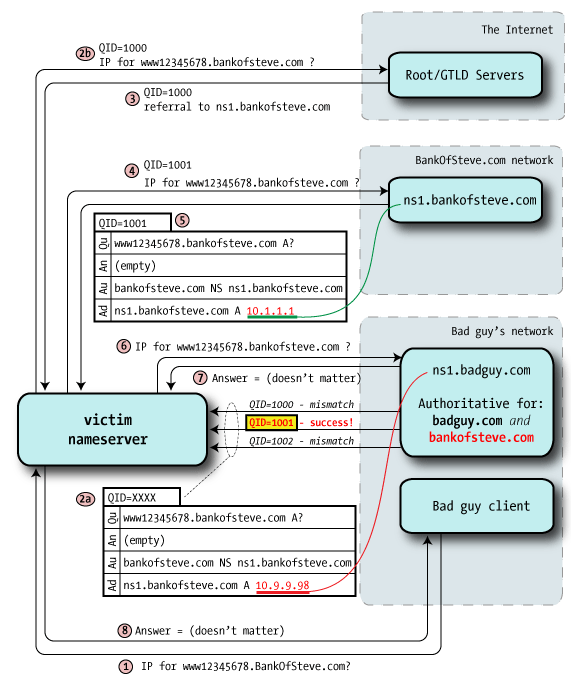
Steve Friedl has a number of excellent technical explanations on his site, and his latest one, An Illustrated Guide to the Kaminsky DNS Vulnerability, is a masterpiece that does a fine job of explaining the DNS vulnerability that Dan Kaminsky found.
Tag: Security
The article Casual Cryptography for Web Developers is probably the nicest, most concise explanation of some of the important crypto principles and practices that web developers will need. Whether you are new to web development, need a refresher or are just curious about the fundamentals, this is one of the best starter articles I’ve seen.
Top 10 Secure Coding Practices
Here’s a list of CERT’s Top 10 Secure Coding Practices. It comes with two bonus secure coding practices (making it an even dozen) and better still, a funny photo that shows that it’s often easier to circumvent rather than defeat security measures.
SecTor Conference
If you’re interested in security and in the Toronto area on November 20 and 21st, the SecTor conference might be for you. Eldon Sprickerhoff tells me that it’s organized by TASK (Toronto Area Security Klatch). Although it’s a local grassroots effort, I’m told that they’ve corralled “a great group of speakers – basically, some of the best speakers from security conferences around the world” to speak at this event.
SecTor takes place on Tuesday, November 20th and Wednesday, November 21st and takes place at the Metro Toronto Convention Centre. Registration is CDN$950, and if you use the promo code “ESENTIRE”, you’ll get a 10% discount.
 By now, you’ve probably heard that for a brief period, a server configuration error caused some Facebook users to see its PHP code rather than the familiar Facebook pages that the code was supposed to render.
By now, you’ve probably heard that for a brief period, a server configuration error caused some Facebook users to see its PHP code rather than the familiar Facebook pages that the code was supposed to render.
How the Code Got Out There
Tony Hung at Deep Jive Interests asked the question “Could a server misconfiguration send out the whole source code in its entirety when you put in the Facebook URL?”
It seems strange that such a simple thing could give away your source, but as anyone who’s set up PHP on a server a number of times will tell you, it can happen.
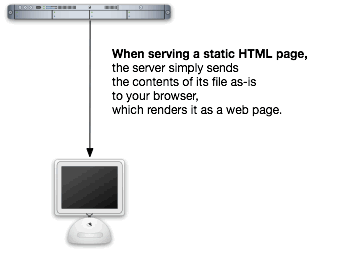
When you visit a static HTML page — that’s a plain old HTML page that wasn’t generated by some server-side script written in PHP or any number of programming languages — the web server simply hands over the contents of the page (the HTML) over to your browser. Your browser renders the HTML as a web page:
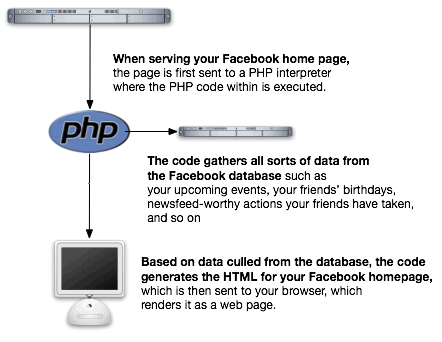
The opposite of a static page is a dynamic one, in which the content is generated on the fly — the server isn’t just handing over the contents of a file. Instead, it calls on some program to cull data from one or more sources and then use that data to assemble some HTML which is then sent to your computer:
What happens when the server is configured incorrectly in such a way that the code for a dynamic page never gets sent through the code interpreter? One common result is that the code gets sent directly to the user. Instead of seeing the result of running the code, the user ends up seeing the code itself. That’s what seems to have happened with Facebook.

Based on a ten-page (!) confession by a former Geek Squad member in which he wrote that Geek Squad agents scour your computer for those porn and personal pictures and videos and copy them onto their thumb drives, Consumerist set up a string operation in which they rigged a computer to record all user activity and brought it in to a number of Best Buy stores to have Geek Squad install iTunes on it.
They report:
We took it to around a dozen Best Buy Geek Squads and asked them to perform simple tasks, like installing iTunes. Most places were fine, sometimes doing the job right on the counter, sometimes even for free.
Click here to see their blog entry and (work-safe) video, and be sure to read these follow-up articles:
- Why We’re Not Telling Geek Squad CEO Which Agent Stole The Porn
- How To Make Your Computer Catch People Stealing Your Porn
There remains one question that I’m sure a lot of guys are asking: Where’d they get that desktop wallpaper image, and could they please share it?