Last night, I attended a special sneak preview for Internet Explorer 8 Beta 2 organized by the folks at High Road Communications, who do the PR for Microsoft here in Toronto. Pete LePage, Product Manager of Internet Explorer Developer Division, did the presentation, and also present were Elliot Katz, Senior Product Manager for Microsoft Canada, Daniel Shapiro, Microsoft Canada’s Audience Manager, and my friend and fellow DemoCamp steward David Crow, Tech Evangelist for Microsoft Canada.
Let me get the disclosure part out of the way. Attending this event got me:
- Free drinks and snacks during the presentation and a free dinner afterwards,
- One Internet Explorer 8 gym water bottle with a tag inside it saying “BPA Free”,
- and one 1GB USB key containing installers for IE8 (pictured in my laptop above) and the IE8 Evaluators’ Guide (a Word document that walks you through IE8’s features).
I’ve been to a couple of these Microsoft events before. The one about their “Windows Live” sites didn’t interest me at all, and the Vista one I attended was largely for people who did IT at companies with 1000 or more employees, which really isn’t my area of interest either (and the Vista preview installer they gave me resulted in disaster). This one was a considerably more interesting, as Pete put on a good presentation and it appears that Microsoft is making an effort to match the competing browsers.
Over the next little while, I’ll post articles covering my experiences as I take IE8 for a spin. In this article, I’ll mostly be talking about InPrivate Browsing, which is colloquially known as “Porn Mode”.
“Porn Mode”, a.k.a. “InPrivate Browsing”
The implementation of a browser session in which history, cache and other “trails of breadcrumbs” are deleted as soon as the session is over isn’t new: Apple’s Safari has a “Private Browsing” feature and there’s a Firefox extension that provides the same utility. However, for those not using Macs and especially those who aren’t the type to download and install Firefox and then install a plugin — and there are lots of these people out there — IE8 may be their first opportunity to try out such a feature.
Banking, Not Wanking
In his presentation, Pete was careful to take the “Banking, not wanking” approach when covering InPrivate Browsing, suggesting all sorts of non-saucy uses for the feature, including doing online banking, shopping for surprise presents for your spouse, surfing from a public terminal and so on. The Microsoft people present took my constant referring to it as “Porn Mode” in great stride, and I thank them for having a sense of humor about it.
The Problem
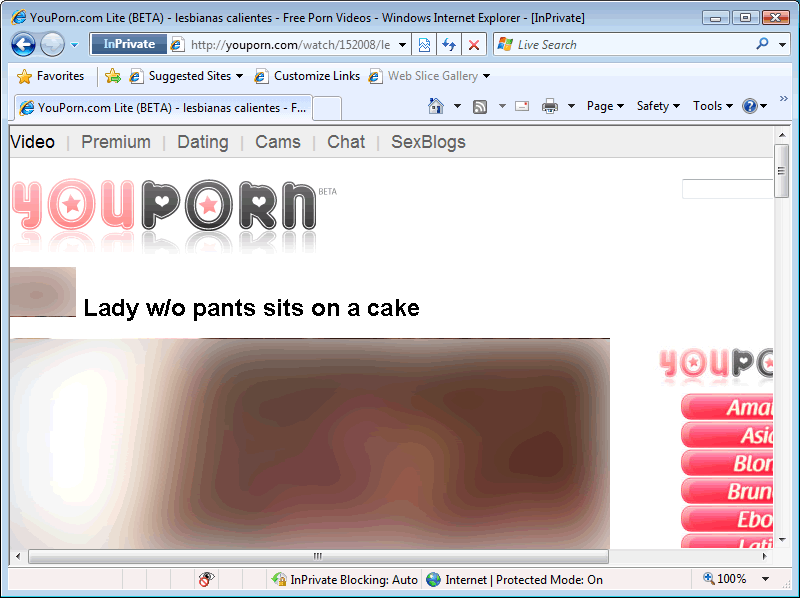
Convenience features like history, cache, automatic username and password field-filling are handy, but they sometimes have unintended consequences. For instance, suppose you, as a healthy, open-minded adult, like to look at videos featuring ladies without pants sitting on cakes at YouPorn.com. Let’s also suppose that a friend asks to borrow your computer for a moment to see a funny cat video at YouTube.com. As your friend types in the letters for “YouTube.com” in the address bar, this happens:
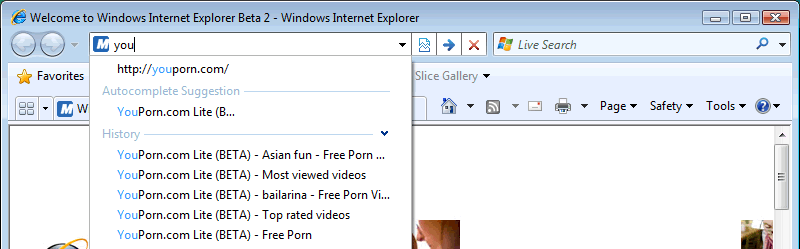
This sort of browser-assisted embarrassment takes place more often than you might think. I’ve seen it happen firsthand, and it’s done everything from causing a little red-facedness to actually thwarting romantic possibilities. And you thought computers were supposed to make our lives easier!
The IE8 solution, InPrivate Browsing, is accessible through the Safety menu (shown below) or through the control-shift-P key combo:
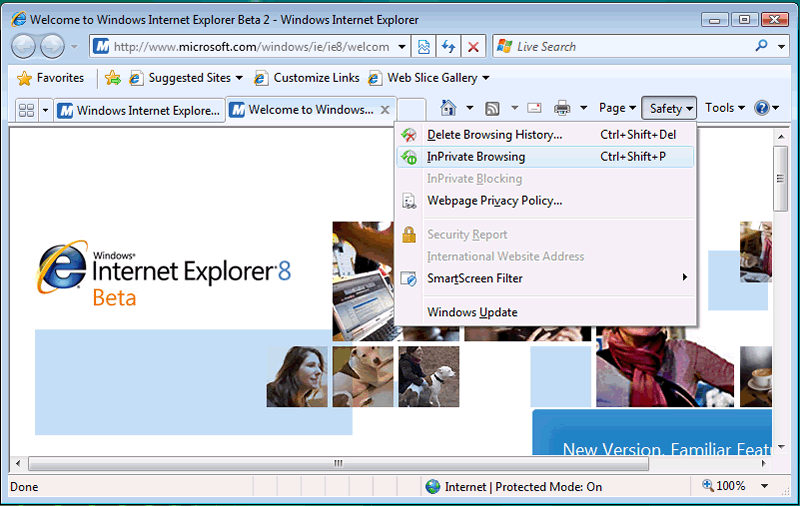
This opens up a new, separate browser window for InPrivate Browsing, which does not keep “breadcrumbs” like history, cache data, cookies and so on. The address bar for InPrivate Browsing windows has the InPrivate logo as a visual cue that this particular session won’t leave a trail that will embarrass you or give away your secrets:
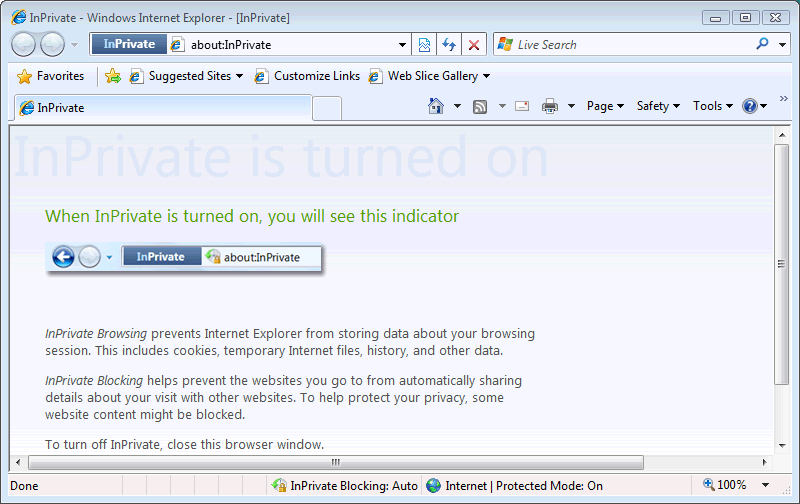
Maybe it’s me, but I think the “InPrivate” graphic in the address bar is a bit too subtle. Then again, a more obvious visual indicator (say, giving the InPrivate browser window a different color) might be an invitation to shoulder-surf.
Hey man, I had to see if it works, right?
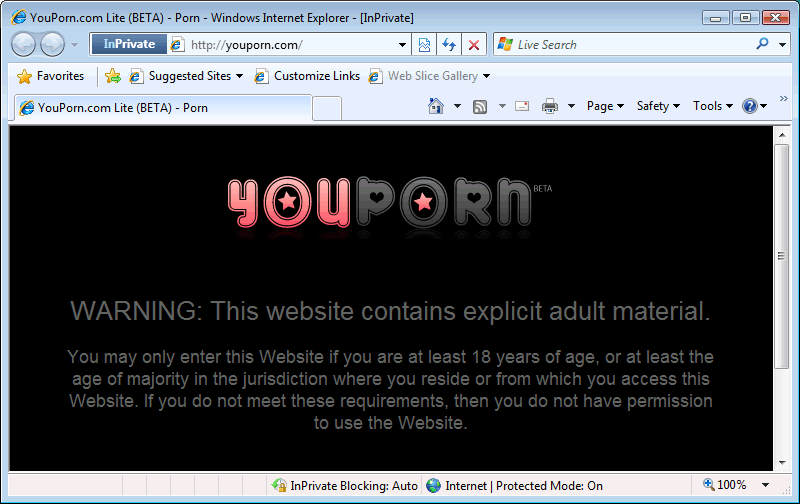
I swear, I had to poke about the site a little bit in order to test if my History was being saved. It’s all in the name of application testing!
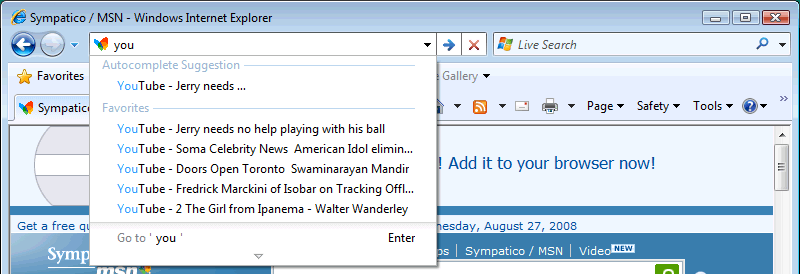
After a little “research”, I closed not just the InPrivate Browsing window, but the whole browser, then started it up again. Then I proceeded to type “You” into the address bar. Under normal circumstances, my YouPorn.com history would be there for all to see. But it wasn’t!
For those of you who need to clear the cache, cookies, history or other data for any reason, there’s also the Delete Browsing History item in the Safety menu:

And it provides a number of deletion options:
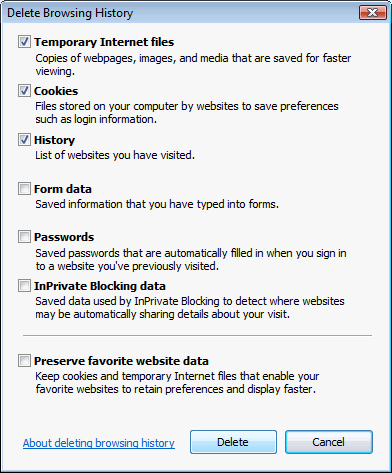
And there you have it: a quick tour of IE8’s much-snickered-about “Porn Mode”.
Keep watching the blog for more posts about IE8 as I use it more and cover its features. Perhaps I’ll cover the development tools next.
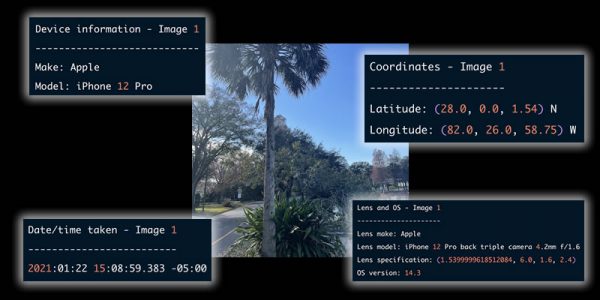
 My latest article on the Auth0 blog, How to Read and Remove Metadata from Your Photos With Python, shows you how to use Python and the exif module to examine, alter, and even remove the metadata that your phone adds to pictures you take.
My latest article on the Auth0 blog, How to Read and Remove Metadata from Your Photos With Python, shows you how to use Python and the exif module to examine, alter, and even remove the metadata that your phone adds to pictures you take. In addition to picture data, photos taken with smartphones and modern digital cameras contain metadata, which is additional information about the photo. This metadata is stored in a format called EXIF, which is short for EXchangeable Image File format, which is a continually evolving standard for information added to digital image and sound recordings.
In addition to picture data, photos taken with smartphones and modern digital cameras contain metadata, which is additional information about the photo. This metadata is stored in a format called EXIF, which is short for EXchangeable Image File format, which is a continually evolving standard for information added to digital image and sound recordings.