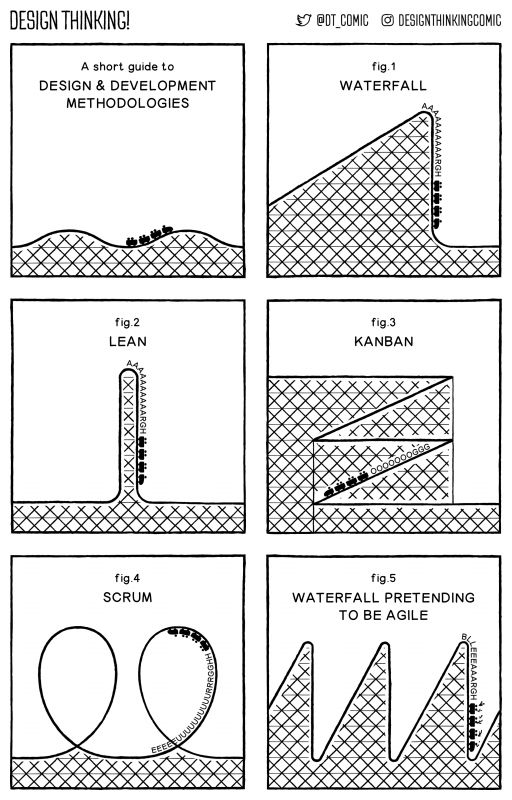
Yet another one we can file under “Funny because it’s true.”

Yet another one we can file under “Funny because it’s true.”

Looking for an interesting online meetup to attend tonight? I’ll be checking out Tampa bay Product Owner Group’s meetup, which has an intriguing title: Stakeholder Management — Tips from FBI Hostage Negotiators. It happens tonight from 6:00 p.m. to 8:00 p.m. on Zoom.
(Here’s the Zoom link for the event.)
Here’s the description of the event, taken straight from their Meetup page:
Product Management IS Stakeholder Management. Influencing and Negotiating is a big part of the role.
In this session, you will learn modern negotiation techniques applied to Stakeholder Management. This is a fun spin on Stakeholder management using the negotiation techniques Chris Voss outlines in “Never Split the Difference.” We explore modern negotiation techniques, then apply them to real-life scenarios.
We examine Mirroring, Labeling, Getting to Yes, and Open-Ended Questions in realistic Product and Stakeholder scenarios. We think we learn by applying, so this will have an interactive element to it!
 Want to know when events like the one above are happening? Join the Tampa Bay Tech Events list and always be informed of what’s coming up in Tampa Bay!
Want to know when events like the one above are happening? Join the Tampa Bay Tech Events list and always be informed of what’s coming up in Tampa Bay!

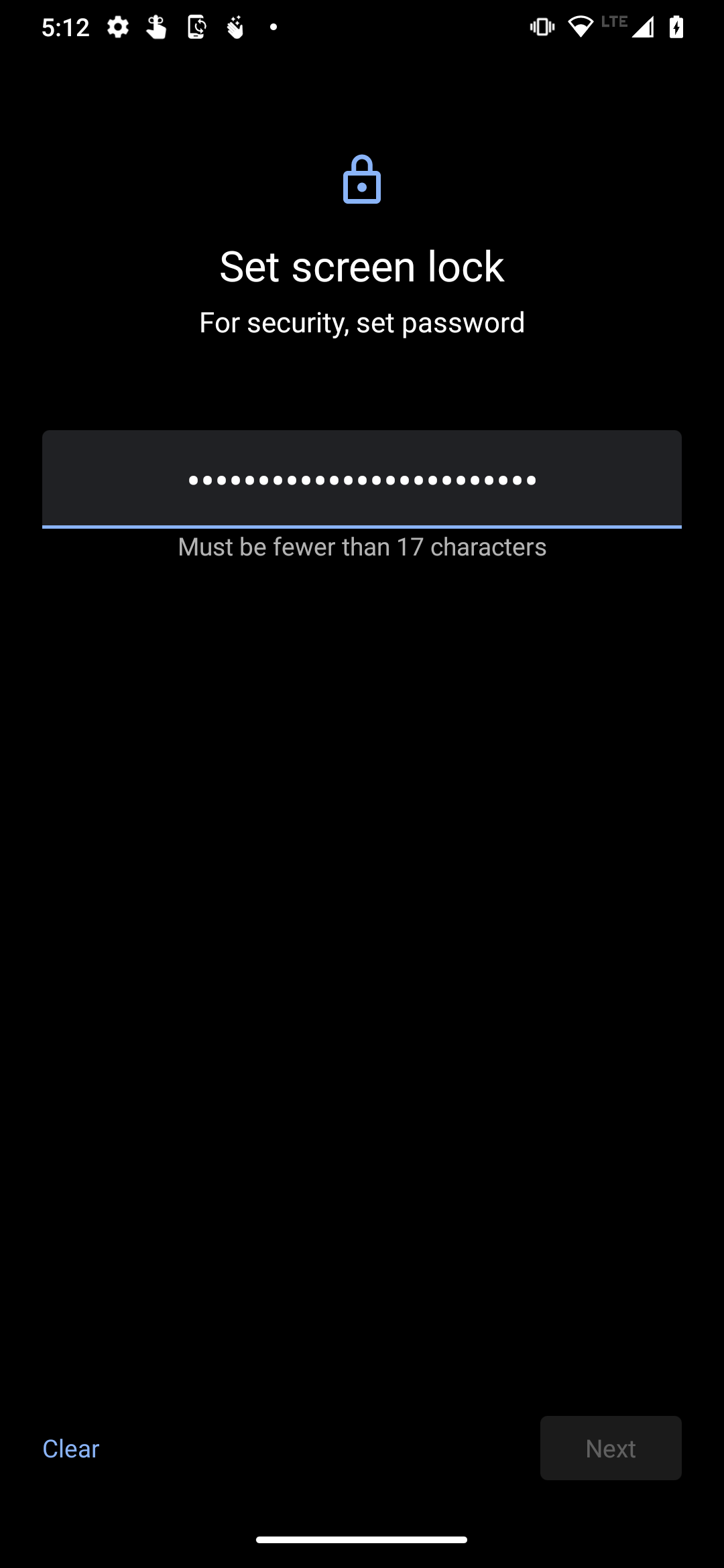 My new Android phone, a Motorola One Hyper, which I wrote about a couple of weeks ago, came out of the box with Android 10.
My new Android phone, a Motorola One Hyper, which I wrote about a couple of weeks ago, came out of the box with Android 10.
When it came time to set the passcode to unlock the phone, I found out that the longest device unlock passcode that even the most recent version of Android will accept is 16 characters. That was the case five years ago, and it’s still the case today.
Android’s “Choose Lock Password” screen is part of AOSP (Android Open Source Project), which means that its source code is easy to find online. It’s ChooseLockPassword.java, and the limitation is a constant defined in a class named ChooseLockPasswordFragment, which defines the portion of the screen where you enter a new passcode.
Here are the lines from that class that define passcode requirements and limitations:
private int mPasswordMinLength = LockPatternUtils.MIN_LOCK_PASSWORD_SIZE; private int mPasswordMaxLength = 16; private int mPasswordMinLetters = 0; private int mPasswordMinUpperCase = 0; private int mPasswordMinLowerCase = 0; private int mPasswordMinSymbols = 0; private int mPasswordMinNumeric = 0; private int mPasswordMinNonLetter = 0;
Note the values assigned to these variables. It turns out that there are only two constraints on Android passcodes that are currently in effect:
mPasswordMinLength, which is set to the value stored in the constant LockPatternUtils.MIN_LOCK_PASSWORD_SIZE. This is currently set to 6.mPasswordMaxLength, which is set to 16.As you might have inferred from the other variable names, there may eventually be other constraints on passcodes — namely, minimums for the number of letters, uppercase letters, lowercase letters, symbol characters, numeric characters, and non-letter characters — but they’re currently not in effect.
16 is a power of 2, and to borrow a line from Snow Crash, powers of 2 are numbers that a programmer would recognize “more readily than his own mother’s date of birth”. This might lead you to believe that 16 characters would be some kind of technical limit or requirement, but…
…Android (and in fact, every current non-homemade operating system) doesn’t store things like passcodes and passwords as-is. Instead, it stores the hashes of those passcodes and passwords. The magic of hash functions is that no matter how short or long the text you feed into them, their output is always the same fixed size (and a relatively compact size, too).
For example, consider SHA-256, from the SHA-2 family of hash functions:
| String value | Its SHA-256 hash |
|---|---|
| (empty string) | e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 |
| x | 2d711642b726b04401627ca9fbac32f5c8530fb1903cc4db02258717921a4881 |
| Chunky bacon! | f0abf4f096ac8fa00b74dbcee6d24c18cfd8ab5409d7867c9767257d78427760 |
| I have come here to chew bubblegum and kick ass… and I’m all out of bubblegum! | 3457314d966ef8d8c66ee00ffbc46c923d1c01adb39723f41ab027012d30f7fd |
| (The full text of T.S. Eliot’s The Love Song of J. Alfred Prufrock) | 569704de8d4a61d5f856ecbd00430cfe70edd0b4f2ecbbc0196eda5622ba71ab |
No matter the length of the input text, the output of the SHA-256 function is always the same length: 64 characters, each one a hexadecimal digit.
Under the 16-character limit, the password will always be shorter than the hash that actually gets stored! There’s also the fact that in a time when storage is measured in gigabytes, we could store a hash that was thousands of characters long and not even notice.
My guess is that the Android passcode size limit of 16 characters is purely arbitrary. Perhaps they thought that 16-character passwords like the ones below were the longest that anyone would want to memorize:
TvsV@PA9UNa$yvNN sDrgjwN#Vc^pmjL4 argmdKAP?!Gzh9mG <Wea2CKufNk+UuU8 EmNv%LN9w4T.sc76
The problem is that it doesn’t account for (theoretically) more secure yet easier to remember passwords of the “correct horse battery staple” method described in the webcomic xkcd, which can easily make passwords longer than 16 characters:
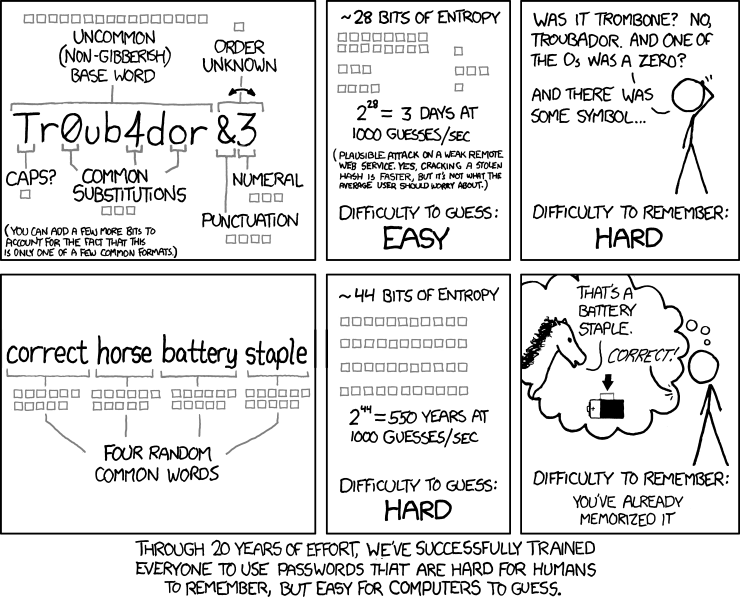
Based on usability factors, there is a point after which a password is just too long, but it’s not 16 characters. I think that iOS’ 37-character limit is more suitable.
For the past four weeks, I’ve been spending over eight hours a day in a classroom in Ybor City, as a student in the inaugural cohort of UC Baseline, the cybersecurity training program offered by Tampa Bay’s security guild, The Undercroft.
We’ve taken the following courses under the tutelage of these instructors:
| Course | Instructor |
|---|---|
| Hardware 101 (5 days) |
Tremere |
| Networking 101 (5 days) |
TreyCraf7 |
| Linux 101 (3 days) |
Cochise |
| Windows 101 (2 days) |
Turtle |
| Infosec 101 (5 days) |
KobyBeefcake TheCleverShark |
There’s just one course left in the program: Python 101, which starts today! Considering that I’ve just come from teaching a Python course to beginners, I suspect that the instructors will have me:
The Python 101 course will run from Monday to Wednesday. After that comes…
…the virtual job fair. The Undercroft will set up online interviews between UC Baseline students/Undercroft guild members and representatives from Tampa Bay security and security-adjacent companies looking to hire. I see some resume editing and LinkedIn profile polishing in my near future.
Friday will be devoted to graduation rituals, which include a solo Capture the Flag competition and a grad barbecue (socially distanced, of course — they’ve got a nice courtyard).
I’m looking forward to the week!

We’re on the back half of Week 3 of UC Baseline, the cybersecurity training program being given by The Undercroft, Tampa Bay’s cybersecurity guild and security-focused coworking space. We just finished three days of Linux 101, which was mostly an intro to command-line Linux, and now it’s time for two days of Windows from a security point of view.

I’m the lucky recipient of a UC Baseline scholarship (I wrote about the scholarship opportunity and then landing it a few weeks back), and I figured that I might as well use my COVID-19 downtime productively by spending five-ish weeks participating in the program.

From the fall of 2008 to the spring of 2011, I ate, slept, and breathed Windows — that’s when I was a developer evangelist for Microsoft Canada. I like to think that I was pretty good at it — good enough that the looney-tunes site TechRights.org saw me as enough of a threat to run a hit piece containing this image:
Since leaving Microsoft, I’ve stayed pretty much outside the Windows world. I call it “time off for good behavior”. I took it to the point that immediately after handing in my blue badge, I drove straight to the store and bought my first iPhone — and remember, I was a designated Windows Phone champ:

This part of the program is being taught by Michael “Turtle” Dorsey, and it’s a great refresher for a lot of material that I haven’t covered in a good long time, since none of my machines runs Windows at the moment (for the class, I’m running Windows 10 in VMWare on my primary Linux laptop).
The class opened with this slide, which I think bodes very well:
